Set Up a Client-Side VPC - AWS
Overview
To securely connect with MarkLogic Data Hub Service over a peered connection, you must set up a client-side VPC (virtual network) and create a peer role that accepts a peering connection from the MarkLogic VPC. Then configure your route tables to enable the client-side VPC and MarkLogic VPC to communicate with each other. For an overview of VPC peering in Amazon Web Services (AWS), see https://aws.amazon.com/blogs/aws/new-vpc-peering-for-the-amazon-virtual-private-cloud/.
Before you begin
You need:
- An AWS account with permissions to create and configure AWS VPCs (virtual networks)
- To subscribe to MarkLogic Data Hub Service (DHS) on AWS
About this task
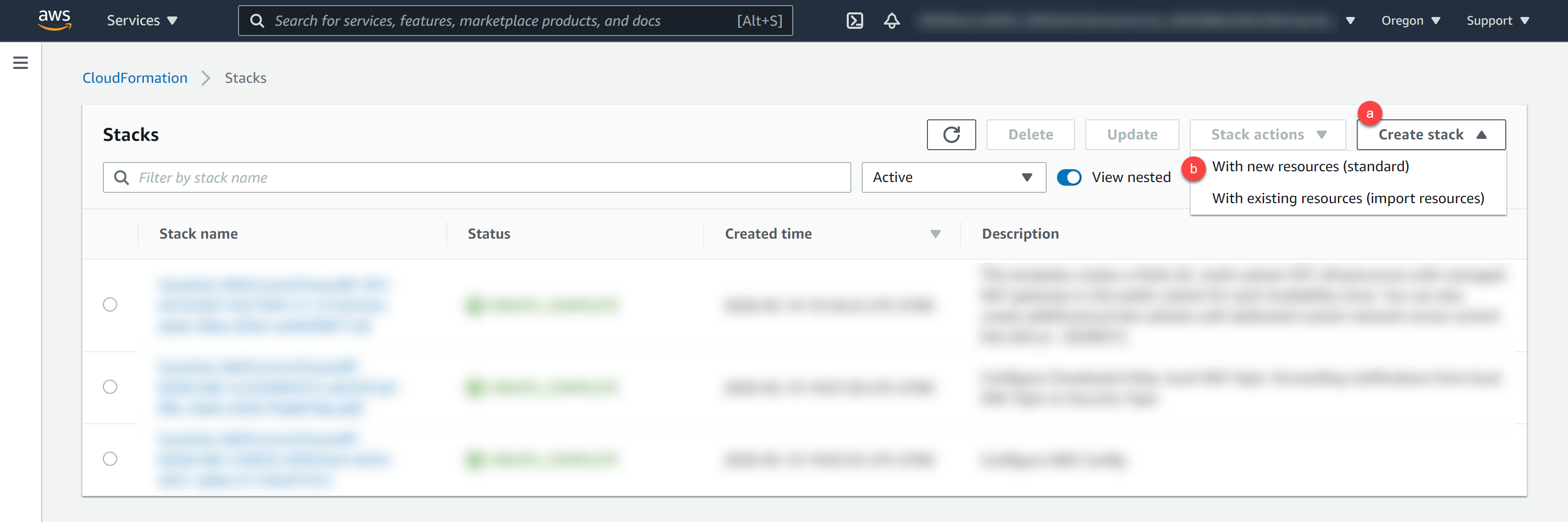
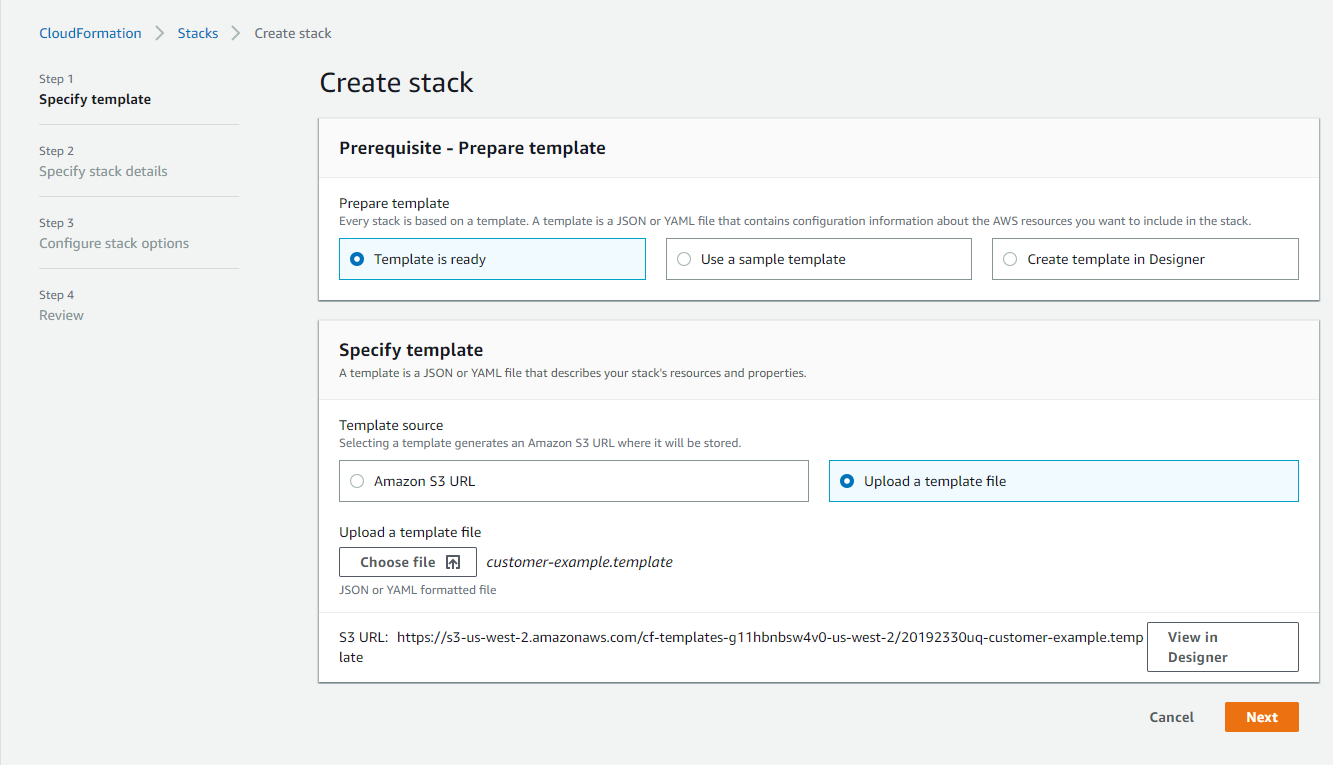
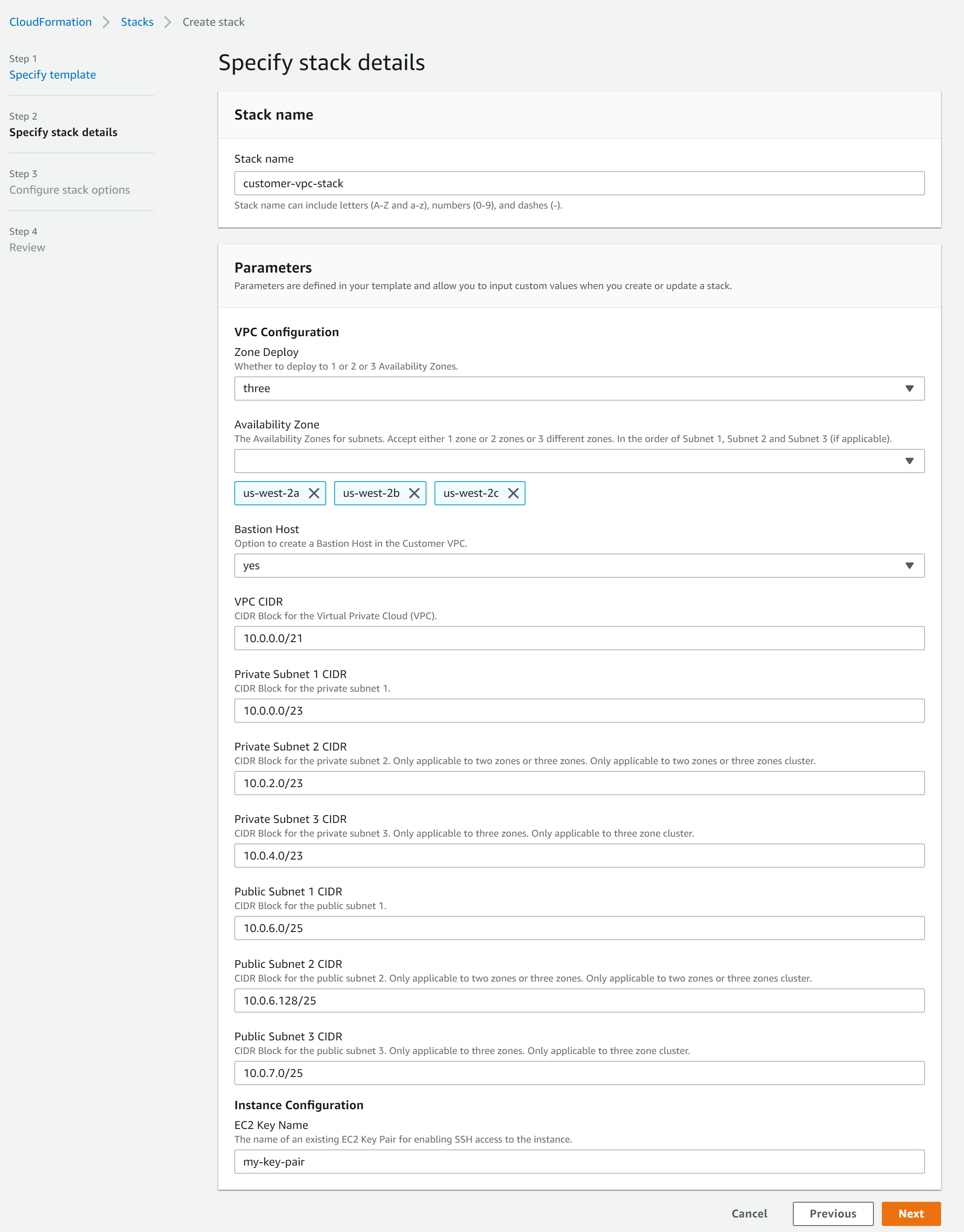
Procedure
Results
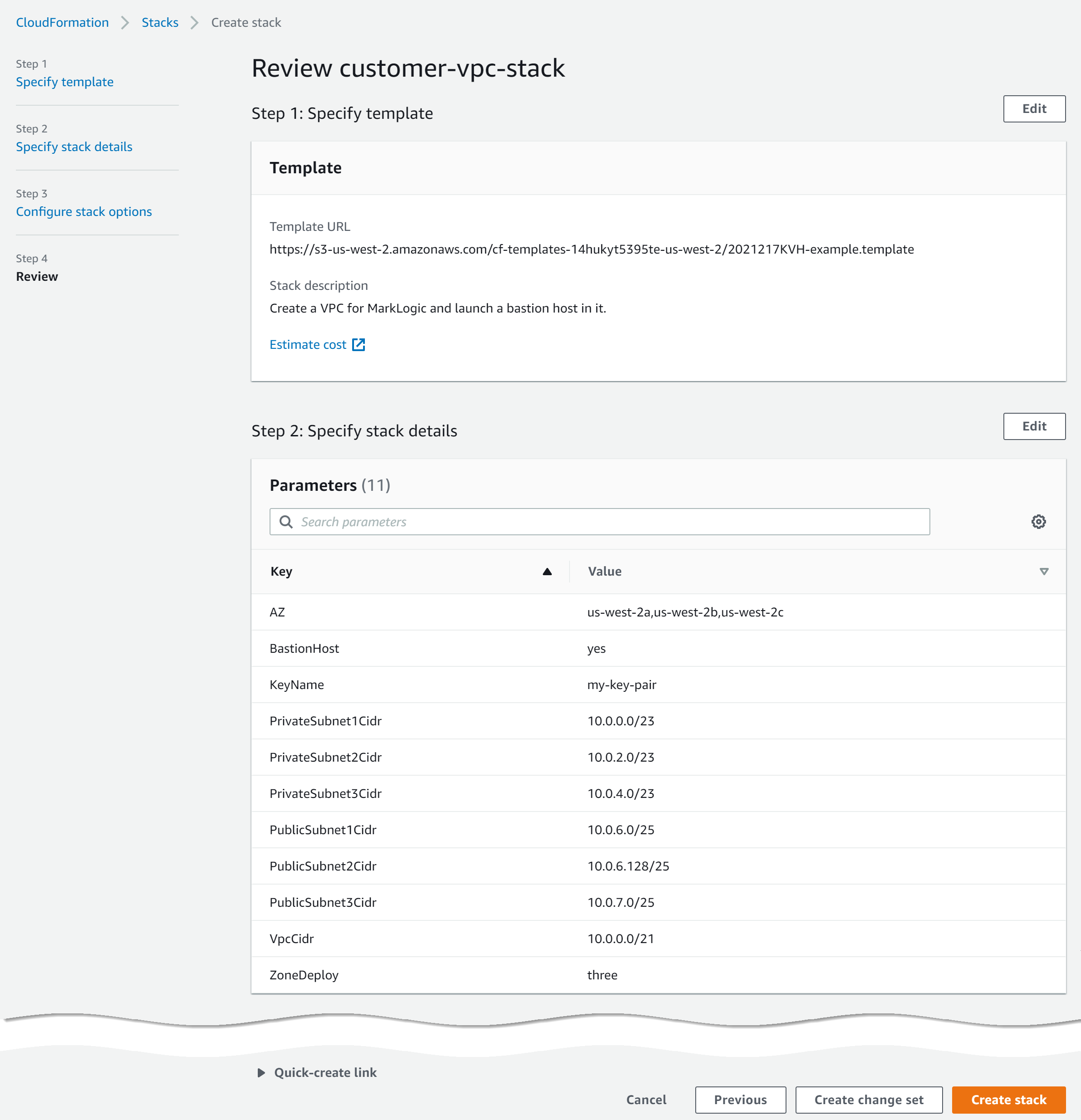
CREATE_COMPLETE.
| Value | How to find | Required to |
|---|---|---|
| Region | For details, see https://docs.aws.amazon.com/emr/latest/ManagementGuide/emr-plan-region.html. | Set Up a Peered Network |
| VPC ID
Note: If using
customer-example.template, this value is also known as MarkLogicVPC. |
In AWS CloudFormation Console, click the stack name and then the Resources tab. Note the value for MarkLogicVPC. Example: For more general information, see https://docs.aws.amazon.com/vpc/latest/userguide/VPC_Subnets.html. |
|
| VPC CIDR | In AWS CloudFormation Console, click the stack name and then click the Parameters tab. Example: For more general information, see https://docs.aws.amazon.com/vpc/latest/userguide/VPC_Subnets.html. |
Set Up a Peered Network |
| Public and Private Subnet CIDRs
Note: In your DHS portal, these values are also known as User Subnet CIDRs.
|
In AWS CloudFormation Console, click the stack name and then click the Parameters tab. Example: For more general information, see https://docs.aws.amazon.com/vpc/latest/userguide/VPC_Subnets.html. |
Set Up a Peered Network |
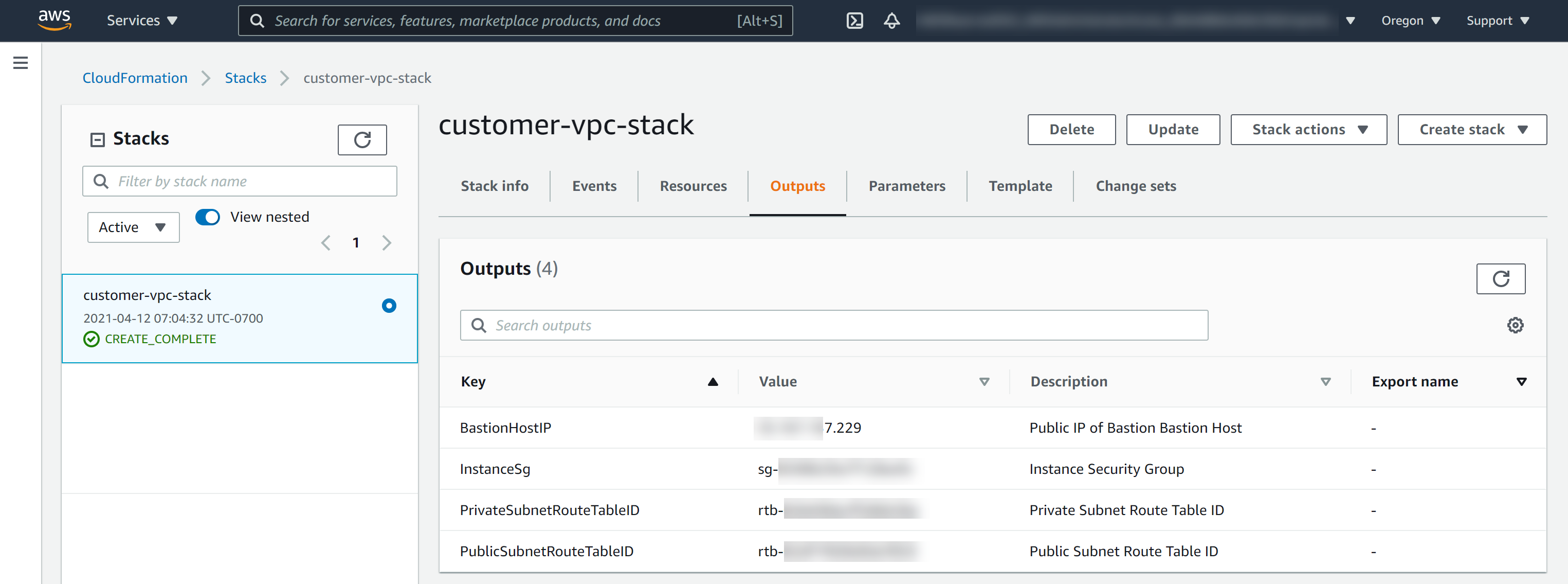
| Public and Private Subnet Route Tables | In AWS CloudFormation Console, click the stack name and then click the Outputs tab. Example: For more general information, see https://docs.aws.amazon.com/vpc/latest/userguide/VPC_Route_Tables.html. |
Configure Your Network Routing |
| BastionHostIP
Note: If configuring SSH tunneling with the script in your DHS portal, this value is also known as BASTION_EC2.
|
In AWS CloudFormation Console, click the stack name and then click the Outputs tab. Note: If you do not use
customer-example.template, locate the IP address of the bastion host you created. |