To use your own Lightweight Directory Access Protocol (LDAP) authentication service, Data Hub Service (DHS) must be able to access your Active Directory (AD).
You must set up your own LDAP server before configuring and creating the DHS instance:
- by setting up VPC peering for the LDAP server, or
- by making your Active Directory publicly visible (Not recommended)
Before you begin
You need:
Peered Track
Public Track
About this task
This task maps Data Hub Service (DHS) instance security roles to LDAP roles with curl commands.
Procedure
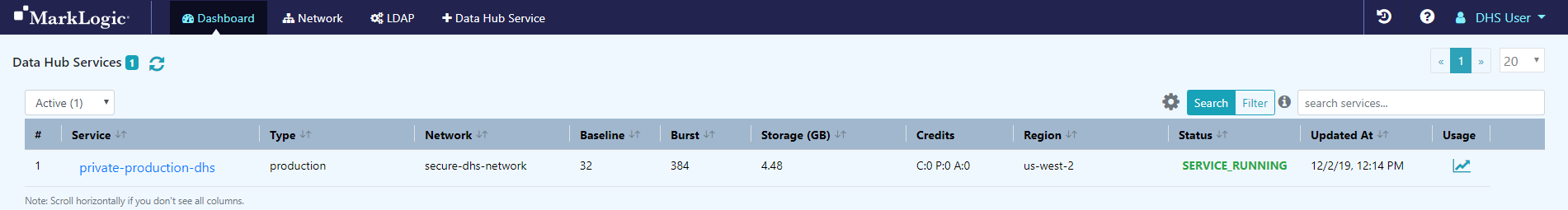
- Go to the MarkLogic Data Hub Service home page.
- Navigate to your DHS instance to authenticate users with your LDAP service.
- In the Service column, click the service name.
Tip: You can customize your dashboard with column sorting, column configuring, and services searching and filtering. See
Customize DHS Dashboard.
- In the Data Hub Service page, click What's next? to display the modal window containing the
curl commands.
- In the modal window, copy the
curl commands to your clipboard:
- highlight and copy the
curl commands, or
- click the copy script icon ()
curl -X POST --anyauth -u USERNAME:PASSWORD -H "Content-Type:application/json" \
-d '{"role-name": "custom-flowDeveloper","role": ["flowDeveloper"],"external-names":[{"external-name":"ROLE_DN"}]}' \
https://4qlvrmylz.rpedmlkv9yy.a.marklogicsvc.com:8002/manage/v2/roles/
curl -X POST --anyauth -u USERNAME:PASSWORD -H "Content-Type:application/json" \
-d '{"role-name": "custom-flowOperator","role": ["flowOperator"],"external-names":[{"external-name":"ROLE_DN"}]}' \
https://4qlvrmylz.rpedmlkv9yy.a.marklogicsvc.com:8002/manage/v2/roles/
curl -X POST --anyauth -u USERNAME:PASSWORD -H "Content-Type:application/json" \
-d '{"role-name": "custom-endpointDeveloper","role": ["endpointDeveloper"],"external-names":[{"external-name":"ROLE_DN"}]}' \
https://4qlvrmylz.rpedmlkv9yy.a.marklogicsvc.com:8002/manage/v2/roles/
curl -X POST --anyauth -u USERNAME:PASSWORD -H "Content-Type:application/json" \
-d '{"role-name": "custom-endpointUser","role": ["endpointUser"],"external-names":[{"external-name":"ROLE_DN"}]}' \
https://4qlvrmylz.rpedmlkv9yy.a.marklogicsvc.com:8002/manage/v2/roles/
curl -X POST --anyauth -u USERNAME:PASSWORD -H "Content-Type:application/json" \
-d '{"role-name": "custom-odbcUser","role": ["odbcUser"],"external-names":[{"external-name":"ROLE_DN"}]}' \
https://4qlvrmylz.rpedmlkv9yy.a.marklogicsvc.com:8002/manage/v2/roles/
See Instance Security Roles for descriptions of each instance security role.
- To edit the
curl commands, paste to a text file.
- In the text file, replace the following parameters per your configuration: USERNAME, PASSWORD, and ROLE_DN
- In the command prompt, run the modified
curl commands.
What to do next
(Optional) If your DHS network is peered, you can configure SSH Tunneling:
Deploy MarkLogic Data Hub and your flows to your cloud environment: