Configure SSH Tunneling with Mac / Linux Using SSH
Overview
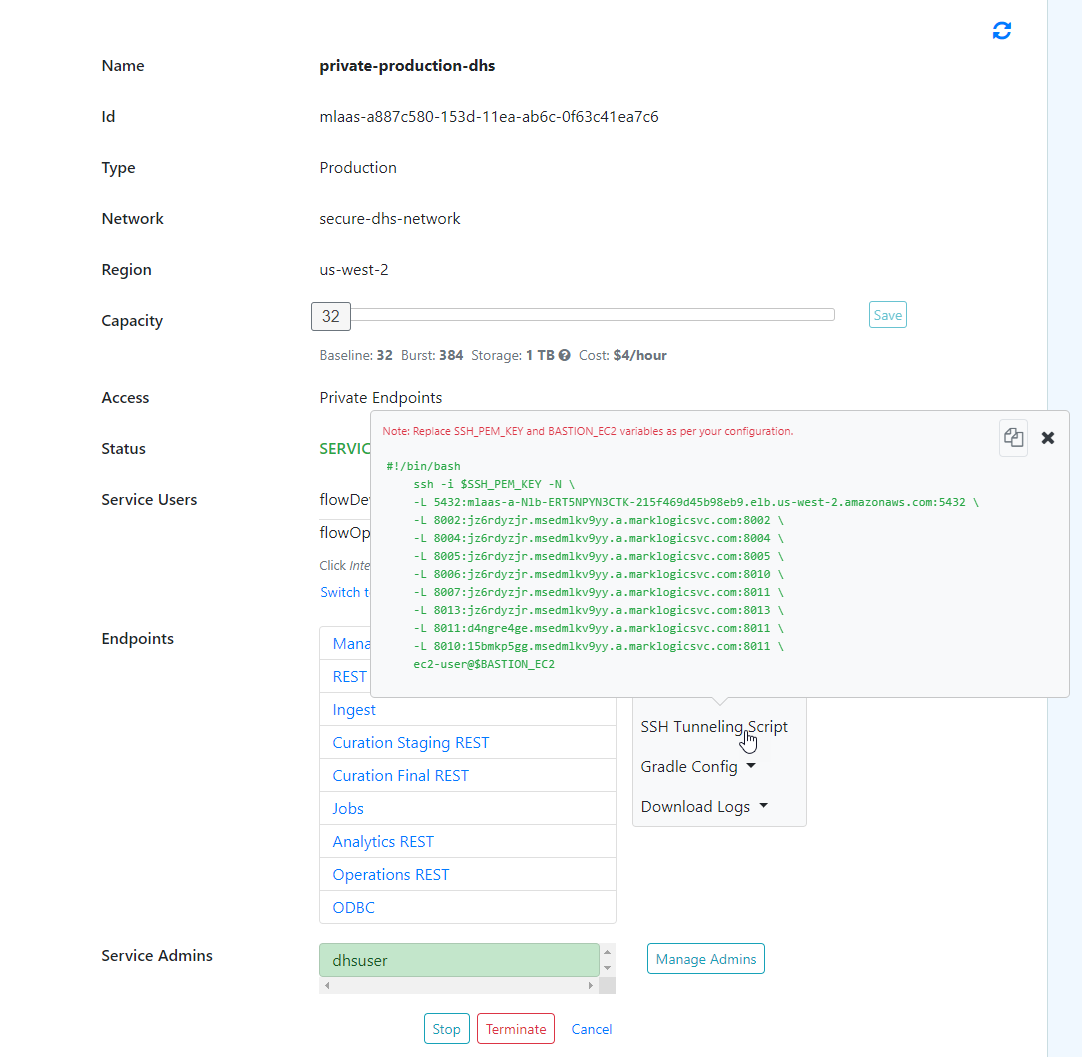
Set up tunneling if you prefer to work directly from your local environment using your own browsers to access the Data Hub Service endpoints.
Before you begin
You need:
- An AWS virtual private cloud (VPC)
- An AWS peer role
- A peered DHS network
- To configure network routing between client-side and DHS networks
- A peered DHS instance
- A DHS instance user account with assigned security roles to internally manage DHS instance users
- (Optional) To add an LDAP configuration to externally manage DHS instance users
About this task
Important: For this task, you must log into your DHS portal with the Security Administrator (SEC-ADMIN) or Service Administrator (SERV-ADMIN) portal role. See Portal Security Roles.
Important: To set up SSH tunneling, your DHS instance must use private endpoints. See Getting Started with Data Hub Service in AWS, and follow the peered configuration.
Procedure
Results
Important: Developers with an existing installation of MarkLogic will notice the potential conflict with use of port 8002. To avoid the conflict, use another port number for the tunnel or change the "Manage" port in your local MarkLogic installation.
What to do next
Deploy MarkLogic Data Hub and your flows to your cloud environment: