| Network |
The name of the preconfigured network to use. The network can be peered or public.
Important: If using a private LDAP server, your LDAP configuration and service must be in the same network.
|
| Region |
Not configurable. The region where your preconfigured network is located. |
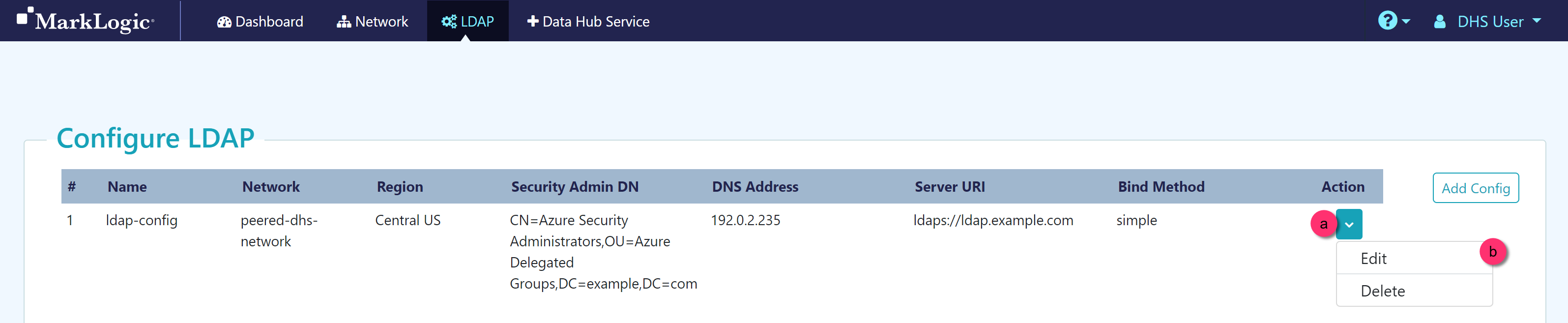
| Name |
Name for this LDAP configuration |
| Security Admin DN |
The distinguished name (DN) for the Security Admin group in your external LDAP server. After you assign an LDAP configuration to a service, the Security Admin DN will be mapped to the data-hub-security-admin service role in the MarkLogic security database. For details about this service role, see Service Roles. Example: CN=Azure Security Administrators,OU=Azure Delegated Groups,DC=example,DC=com
Important: Only users in your external LDAP server assigned the data-hub-security-admin service role can execute the curl commands that map service roles to LDAP roles. For details, see Service Roles.
Tip: A Distinguished Name (DN) is a sequence of Relative Distinguished Names (RDNs), which are attributes with associated values expressed by the form attribute=value. Each RDN attribute is separated by a comma in a DN. For details on LDAP DNs, see http://www.rfc-editor.org/rfc/rfc4514.txt.
|
| DNS Address |
The IP address of your external LDAP server. The DNS Address can be public or private, and include more than one IP address. Example: 192.0.2.235
Important: If using more than one IP address, separate each IP address with a comma. Example: 192.0.2.235,198.51.100.234
|
| Server URI |
The URI of your external LDAP server. Must include either the ldap:// or ldaps:// prefix. Example: ldaps://ldap.example.com
Note: The URI must not contain a port number.
The port number is defined by the prefix.
| URI Prefix |
Port Number |
| ldap:// |
389 |
| ldaps:// |
636 |
|
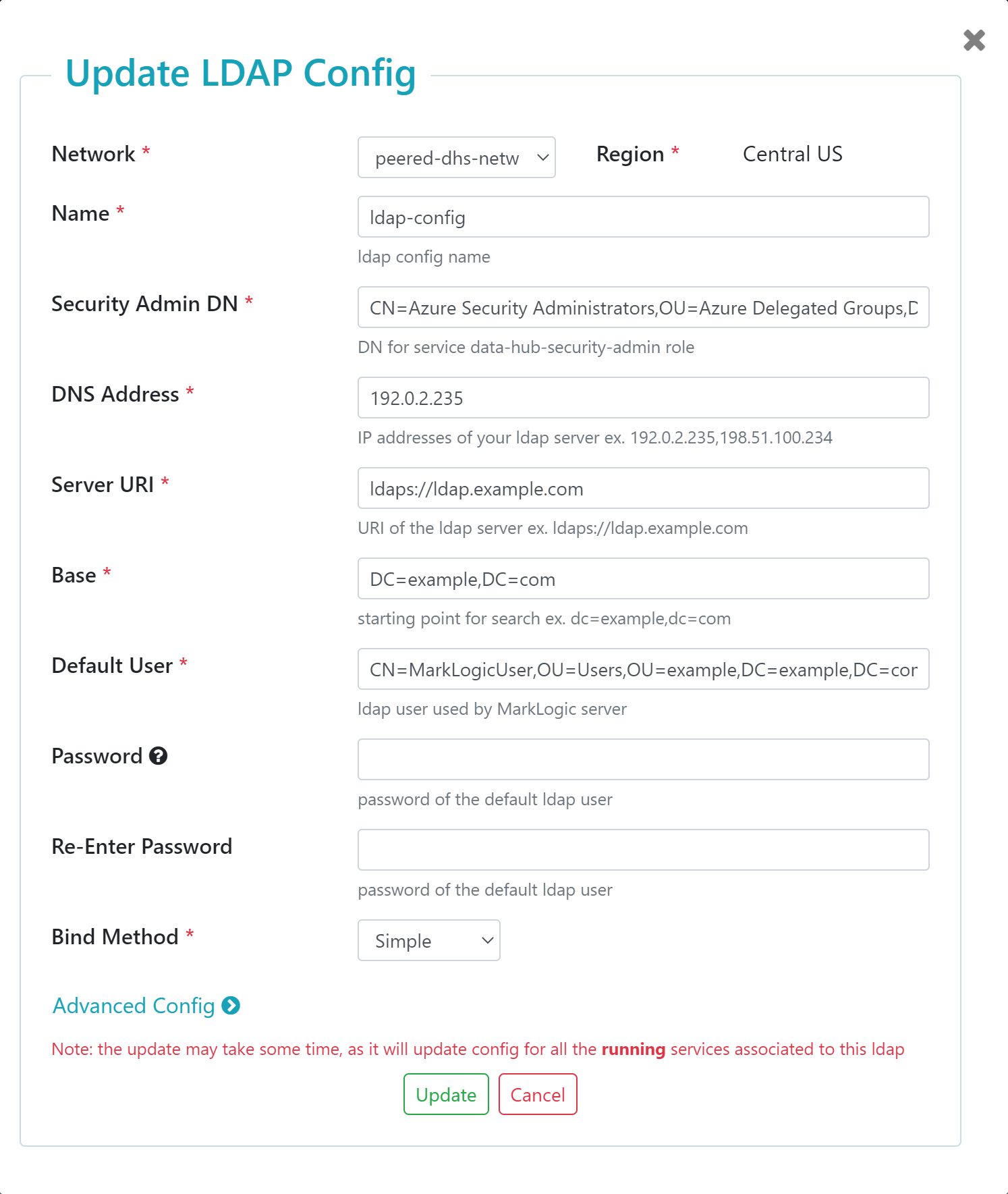
| Base |
The location in your external LDAP server's directory information tree where MarkLogic will begin searching for DNs. Example: DC=example,DC=com |
| Default User |
The DN for the user in your external LDAP server that MarkLogic uses to search your external LDAP server. MarkLogic uses the Default User to locate DNs that match the external names (ROLE_DN) you provided. If Bind is set to Simple, Default User must be entered as a DN. Example: CN=MarkLogicUser,OU=Users,OU=example,DC=example,DC=com
Important: Default User must be able to access the Base DN.
|
| Password / Re-Enter Password |
The password for the Default User. Provide the password you defined for this user in your external LDAP server. |
| Bind Method |
The bind method to use. Default: Simple |