Set Up MarkLogic Server Encryption
Before you set up encryption at rest, be sure that your cluster has upgraded to MarkLogic Server 9. If the cluster has not been upgraded, the encryption feature will not be available.
Set up your external KMS, if not already set up. See Set Up an External KMIP KMS with MarkLogic Server Encryption for details.
Get the generated encryption key IDs from the external KMS (for data, config, and logs as needed). If you are using data encryption, configuration file encryption, and log encryption, and you want different encryption keys for each, you will need three encryption key IDs (UUIDs).
Click Clusters in the left navigation tree, then click the name of the cluster to configure.
Click the Keystore tab, then click the external radio button next to Key Management System (KMS). Additional fields for setting up the external KMS are displayed.
Provide the host name and port number for your external KMS in the appropriate fields.
Note
Replace the existing host name, port, and encryption key IDs with the information for the external KMS.
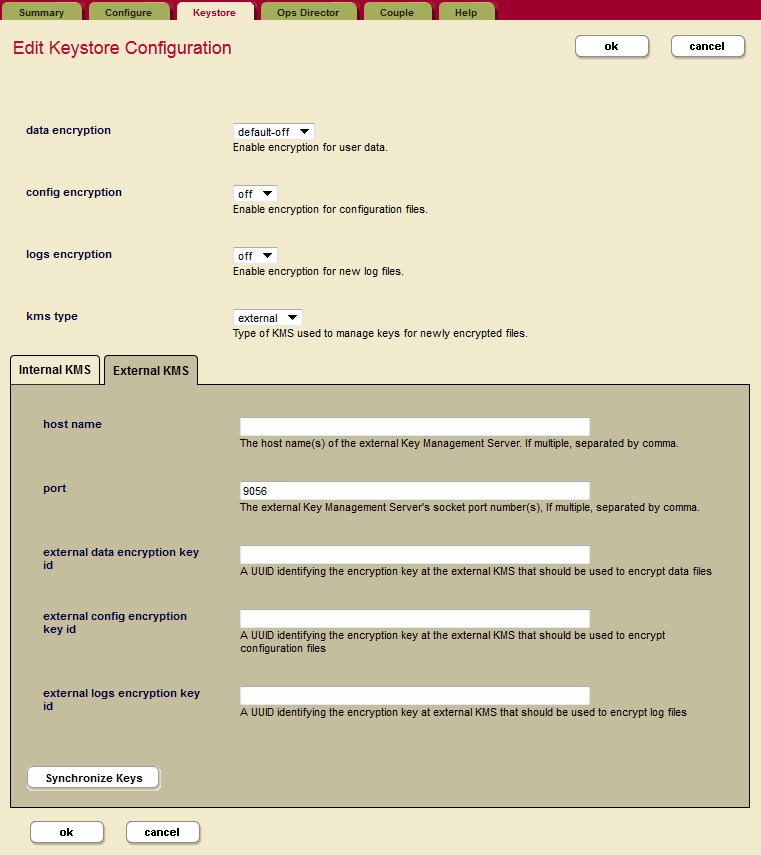
Add the encryption key IDs (generated by the external KMS) for the types of encryption you are configuring (data, configuration, and/or logs), to the appropriate fields on the Edit Keystore Configuration page in the Admin Interface.
Click OK.
Turn on the types of encryption you wish from Admin Interface (data encryption, configuration file encryption, and/or log file encryption).
Note
Adding the encryption information will require a restart of all of the hosts in your cluster.
When using an external KMS, key encryption keys (KEK) might be rotated according to the policy set in the KMS. Each time that the keys are rotated in an external KMS, you will have to update the new KEK IDs (UUIDs - like key encryption keys - KEKs) to MarkLogic Server. Data will then start to be encrypted with new KEK ID, as described in Key Rotation. The object keys (OKEYs) with be enveloped by the external KMS and the new keys as MarkLogic Server uses the IDs to request that the OKEY be enveloped with the corresponding KEK ID.
Encryption at rest may be configured using REST, XQuery, or JavaScript APIs. See APIs for Encryption at Rest for details.