Key Rotation
For the internal wallet, key encryption keys (KEK) can be manually rotated. Keys can be manually rotated at regular intervals or if an encryption key has been compromised. This type of key rotation can be triggered on individual encryption categories (configuration, data, logs) using MarkLogic Server built-in functions.
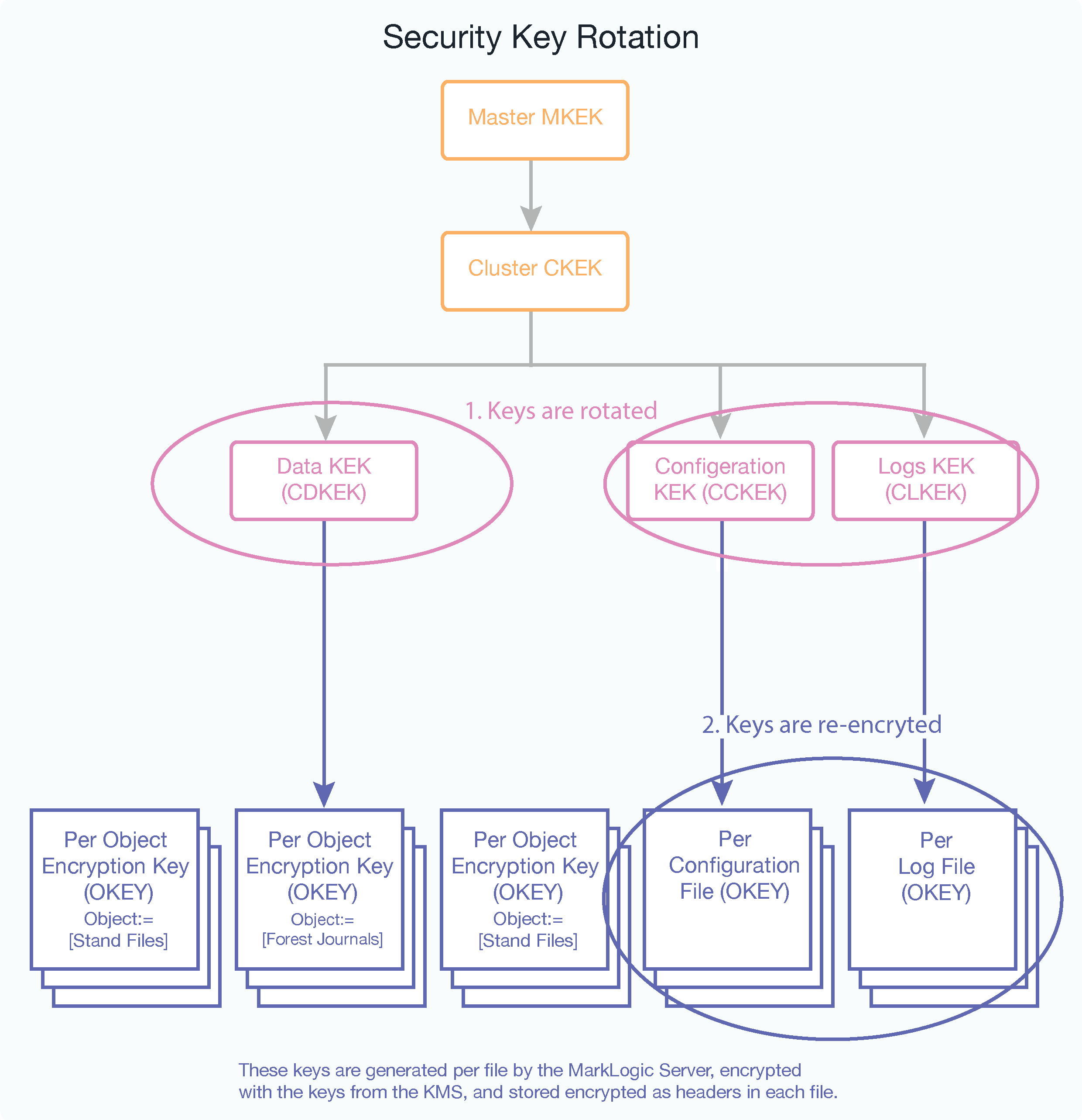
There are two steps to key rotation. First, rotating the KEK keys (using AES 256 symmetric encryption) used to envelope the object file encryption keys, and second, re-encrypting the object file encryption keys (also using AES 256 symmetric encryption).
After calling the built-in function to rotate encryption keys, all new data will be written to disk using the new key encryption key. Old data will be migrated as it is re-written to disk. If you wish to force re-encryption using the new key, you can either force a merge or re-index the forest.
At the local, host level, you can manually rotate the data keys, configuration keys, and the logs keys (CDKEK, CCKEK, CLKEK) using these APIs:
Note
These key rotation functions are only available for the MarkLogic Server internal KMS (the PKCS #11 secured wallet) and not for any keys that are managed by an external KMS.
At the cluster level, to manually rotate the cluster-level keys use these APIs:
Note
When you are using an external KMS, MarkLogic Server does not have access to the envelope key, it only has access to the key ID, and asks for the KMS to open the envelope.