Security Guide — Chapter 18
Sample Security Scenarios
This chapter describes some common scenarios for defining security policies in your applications. The scenarios shown here are by no means exhaustive. There are many possibilities for how to set up security in your applications. The following sections are included:
- Protecting the Execution of XQuery Modules
- Choosing the Access Control for an Application
- Implementing Security for a Read-Only User
Protecting the Execution of XQuery Modules
One simple way to restrict access to your MarkLogic Server application is to limit the users that have permission to run the application. If you load your Xquery code into a modules database, you can use an execute permission on the XQuery document itself to control who can run it. Then, a user must possess execute permissions to run the module. To set up a module to do this, perform the following steps:
- Using the Admin Interface, specify a modules database in the configuration for the App Server (HTTP or WebDAV) that controls the execution of your XQuery module.
- Load the XQuery module into the modules database, using a URI with an
.xqyextension, for examplemy_module.xqy. - Set
executepermissions on the XQuery document for a given role. For example, if you want users with therun_applicationrole to be able to execute an XQuery module with the URIhttp://modules/my_module.xqy,xdmp:document-set-permissions("http://modules/my_module.xqy", xdmp:permission("run_application", "execute") )
- Create the
run_applicationrole. - Assign the
run_applicationrole to the users who can run this application.
Now only users with the run_application role can execute this document.
Because your application could also contain amped functions, this technique can help restrict access to applications that use amps.
Choosing the Access Control for an Application
The role-based security model in MarkLogic Server combined with the supported authentication schemes provides numerous options for implementing application access control. This section describes common application access control alternatives:
- Open Access, No Log In
- Providing Uniform Access to All Authenticated Users
- Limiting Access to a Subset of Users
- Using Custom Login Pages
- Access Control Based on Client IP Address
For details on the different authentication schemes, see Types of Authentication.
Open Access, No Log In
This approach may be appropriate if security is not a concern for your MarkLogic Server implementation or if you are just getting started and want to explore the capabilities of MarkLogic Server before contemplating your security architecture. This scenario provides all of your users with the admin role.
You can turn off access control for each HTTP or WebDAV server individually by following these steps using the Admin Interface:
- Go to the Configure tab for the HTTP server for which you want to turn off access control.
- Scroll down to the authentication field and choose
application-levelfor the authentication scheme. - Choose a user with the
adminrole for the default user. For example, you may choose theadminuser you created when you installed MarkLogic.To assist with identifying users with the
adminrole, the default user selection field places (admin) next toadminusers.
In this scenario, all users accessing the application server are automatically logged in with a user that has the admin role. By default, the admin role has the privileges and permissions to perform any action and access any document in the server. Therefore, security is essentially turned off for the application. All users have full access to the application and database associated with the application server.
Providing Uniform Access to All Authenticated Users
This approach allows you to restrict application access to users in your security database, and gives those users full access to all application servers defined in MarkLogic Server. There are multiple ways to achieve the same objective but this is the simplest way.
- In the Admin Interface, go to the Users tab under Security.
- Give all users in the security database the
adminrole. - Go to the Configuration tab for all HTTP and WebDAV servers in the system.
- Go to the authentication field and choose
digest,basicordigest-basicauthentication. - Leave the privilege field blank since it has no effect in this scenario. This field specifies the privilege that is needed to log into application server. However, the users are assigned the
adminrole and are treated as having all privileges.
In this scenario, all users must authenticate with a username and password. Once they are authenticated, however, they have full access to all functions and data in the server.
Limiting Access to a Subset of Users
This application access control method can be modified or extended to meet the requirements in many application scenarios. It uses more of the available security features and therefore requires a better understanding of the security model.
To limit application access to a subset of the users in the security database, perform the following steps using the Admin Interface:
- Create an execute privilege named
exe-priv-app1to represent the privilege to access the App Server. - Create a role named
role-app1that hasexe-priv-app1execute privilege. - Add
role-app1to the roles of all users in the security database who should have access to this App Server. - In the Configuration page for this App Server, scroll down to the authentication field and select
digest,basicordigest-basic. If you want to use application-level authentication to achieve the same objective, a custom login page is required. See the next section for details. - Select
exe-priv-app1for the privilege field. Once this is done, only the users who have theexe-priv-app1by virtue of their role(s) are able to access this App Server.If you want any user in the security database to be able to access the application, leave the privilege field blank.
At this point, the application access control is configured.
This method of authentication also needs to be accompanied by the appropriate security configuration for both users and documents associated with this App Server. For example, functions such as xdmp:document-insert and xdmp:document-loadthrow exceptions unless the user possesses the appropriate execute privileges. Also, users must have the appropriate default permissions (or specify the appropriate permissions with the API) when creating new documents in a database. Documents created by a user who does not have the admin role must be created with at least one update permission or else the transaction throws an XDMP-MUSTHAVEUPDATE exception. The update permission is required because otherwise once the documents are created no user (except users with the admin role) would be able to access them, including the user who created them.
Using Custom Login Pages
Digest and basic authentication use the browser's username and password prompt to obtain user credentials. The server then authenticates the credentials against the security database. There is no good way to create a custom login page using digest and basic authentication. To create custom login pages, you need to use application-level authentication.
To configure MarkLogic Server to use a custom login page for an App Server, perform the following steps using the Admin Interface:
- Go to the Configuration tab for the HTTP App Server for which you want to create a custom login page.
- Scroll down to the authentication field and select application-level.
- Choose
nobodyas the default user. Thenobodyuser is automatically created when MarkLogic Server is installed. It is created with the following roles:rest-reader, rest-extension-user, app-user, harmonized-readerand is given a password which is randomly generated. - Create a custom login page that meets your needs. We refer to this page as
login.xqy. - Make
login.xqythe default page displayed by the application server. Do not require any privilege to accesslogin.xqy(that is, do not placexdmp:security-assert()in the beginning of the code forlogin.xqy. This makeslogin.xqyaccessible bynobody, the default user specified above, until the actual user logs in with his credentials.
login.xqy page likely contains a snippet of code as shown below:...return if xdmp:login($username, $password) then ... protected page goes here... else ... redirect to login page or display error page...The rest of this example assumes that all valid users can access all the pages and functions within the application.
If you are using a modules database to store your code, the login.xqy file still needs to have an execute permission that allows the nobody (or whichever is the default) user to access the module. For example, you can put an execute permission paired with the app-user role on the login.xqy module document, and make sure the nobody user has the app-user role (which it does by default).
- Create a role called
application-user-role. - Create an execute privilege called
application-privilege. Add this privilege to theapplication-user-role. - Add the
application-user-roleto all users who are allowed to access the application. - Add this snippet of code before the code that displays each of the pages in the application, except for
login.xqy:try { xdmp:security-assert("application-privilege","execute") } catch($e) { xdmp:redirect-response("login.xqy") }
if(not(xdmp:has-privilege("application-privilege","execute"))) then ( xdmp:redirect-response("login.xqy") ) else ()
This ensures that only a user who has the application-privilege by virtue of his role can access these protected pages.
Similar to the previous approach, this method of authentication requires the appropriate security configuration for users and documents. See Introduction to Security for background on the security model.
Access Control Based on Client IP Address
MarkLogic Server supports deployments in which a user is automatically given access to the application based on the client IP address.
Consider a scenario in which a user is automatically logged in if he is accessing the application locally (as local-user) or from an approved subnet (as site-user). Otherwise, the user is asked to login explicitly. The steps below describe how to configure MarkLogic Server to achieve this access control.
- Using the Admin Interface, configure the App Server to use a custom login page:
- Go to the Configuration tab for the HTTP or WebDAV App Server for which you want to create a custom login page.
- Scroll down to the authentication field and select application-level.
- For this example, choose
nobodyas the default user. Thenobodyuser is automatically created when MarkLogic Server is installed. It is created with the following roles:rest-reader, rest-extension-user, app-user, harmonized-readerand is given a password which is randomly generated.
- Add the following code snippet to the beginning of the default page displayed by the application, for example,
default.xqy.xquery version "1.0-ml" declare namespace widget ="http://widget.com" import module "http://widget.com" at "/login-routine.xqy" let $login := widget:try-ip-login() return if($login) then <html> <body> The protected page goes here. You are {xdmp:get-current-user()} </body> </html> else xdmp:redirect-response("login.xqy")
The try-ip-login function is defined in login-routine.xqy. It is used to determine if the user can be automatically logged in based on the client IP address. If the user cannot be logged in automatically, he is redirected to a login page called login.xqy where he has to log in explicitly. See Using Custom Login Pages for example code for login.xqy.
- Define
try-ip-login:- Create a file named
login-routine.xqyand place the file in theModulesdirectory within the MarkLogic Server program directory. You create an amp fortry-ip-logininlogin-routine.xqyin the next code sample. For security reasons, all amped functions must be located in the specifiedModulesdirectory or in theModulesdatabase for the App Server. - Add the following code to
login-routine.xqy:xquery version "1.0-ml" module "http://widget.com" declare namespace widget ="http://widget.com"define function try-ip-login()as xs:boolean { let $ip := xdmp:get-request-client-address() return if(compare($ip,"127.0.0.1") eq 0) then (:local host:) xdmp:login("localuser",()) else if(starts-with($ip,<approved-subnet>)) then xdmp:login("site-user",()) else false() }
- Create a file named
If the user is accessing the application from an approved IP address, try-ip-login logs in the user with username local-user or site-user as appropriate and returns true. Otherwise, try-ip-login returns false.
In the code snippet above, the empty sequence () is supplied in place of the actual passwords for local-user and site-user. The pre-defined xdmp-login execute privilege grants the right to call xdmp:login without the actual password. This makes it possible to create deployments in which users can be automatically logged in without storing user passwords outside the system.
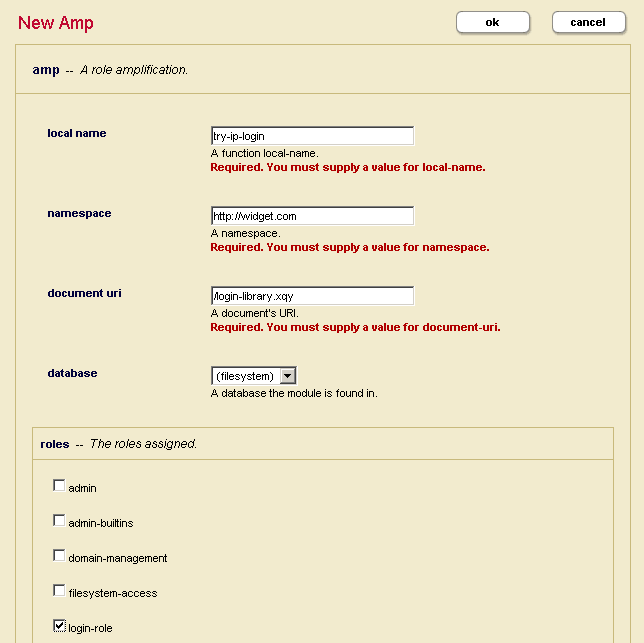
- Finally, to ensure that the code snippet above is called with the requisite xdmp-login privilege, configure an amp for
try-ip-login:- Using the Admin Interface, create a role called
login-role. - Assign the pre-defined
xdmp-loginexecute privilege tologin-role. Thexdmp-loginprivilege gives a user of thelogin-rolethe right to call xdmp:login for any user without supplying the password. - Create an amp for try-ip-login as shown below:
- Using the Admin Interface, create a role called
An amp temporarily assigns additional role(s) to a user only for the execution of the specified function. The amp above gives any user who is executing try-ip-login() the login-role temporarily for the execution of the function.
In this example, default.xqy is executed as nobody, the default user for the application. When the try-ip-login function is called, the nobody user is temporarily amped to the login-role. The nobody user is temporarily assigned the xdmp:login execute privilege by virtue of the login-role. This enables nobody to call xdmp:login in try-ip-login for any user without the corresponding password. Once the login process is completed, the user can access the application with the permissions and privileges of local-user or site-user as appropriate.
- The remainder of the example assumes that
local-userandsite-usercan access all the pages and functions within the application.- Create a role called
application-user-role. - Create an execute privilege called
application-privilege. Add this privilege to theapplication-user-role. - Add the
application-user-roletolocal-userandsite-user. - Add this snippet of code before the code that displays each of the subsequent pages in the application:
try { xdmp:security-assert("application-privilege","execute") ... } catch($e) { xdmp:redirect-response("login.xqy") }
- Create a role called
if(not(xdmp:has-privilege("application-privilege","execute"))) then ( xdmp:redirect-response("login.xqy") ) else ()
This ensures that only the user who has the application-privilege by virtue of his role can access these protected pages.
Implementing Security for a Read-Only User
In this scenario, assume that you want to implement a security model that enables your users to run any XQuery code stored in the modules database for a specific App Server with read-only permissions on all documents in the database.
Reviewing the MarkLogic security model, recall that users do not have permissions, documents have permissions. And permissions are made up of a role paired with a capability. Additionally, execute privileges protect code execution and URI privileges protect the creation of documents in a specific URI namespace. This example shows one way to implement the read-only user and is devided into the following parts:
Steps For Example Setup
To set up this example scenario, perform the following steps, using the Admin Interface:
- Create a role named
ReadsStuff. - Create a user named
ReadOnlyand grant this user theReadsStuffrole. - Create a role named
WritesStuffand grant this role theReadsStuffrole. - Grant the
WritesStuffrole theany-uriprivilege, as well as any execute privileges needed for your application code. - Create a user named
LoadsStuffand grant this user theWritesStuffrole. When you load documents, load them as theLoadsStuffuser and give each document an update and insert permission for theWritesStuffrole and a read permission for theReadsStuffrole.Here is sample code to create a set of permissions to do this as on option to either the
xdmp:document-insertfunction or thexdmp:document-loadfunction:(xdmp:permission("ReadsStuff", "read"), xdmp:permission("WritesStuff", "insert"), xdmp:permission("WritesStuff", "update"))
An alternative to specifying the permissions when you load documents is to assign default permissions to the LoadsStuff user or the WritesStuff role.
Troubleshooting Tips
If you are running a URL rewriter (or an error handler), you need to give the ReadsStuff role to the nobody user or whichever user is the default user for your App Server. When the URL rewriter executes, the request has not yet been authenticated, so it runs as the default user. The default user is nobody unless you have specified a different default for your App Server. The best practice is to create another role, for example my-app-user and add an execute permission for the URL rewriter and your error handler (if any) for the my-app-user role. This is better because you do not want the nobody user to have access to your database.