How MarkLogic Server Authenticates and Authorizes a User
This flowchart illustrates the logic that MarkLogic Server follows to determine how to authenticate an internal user and how to authenticate then authorize an external user:
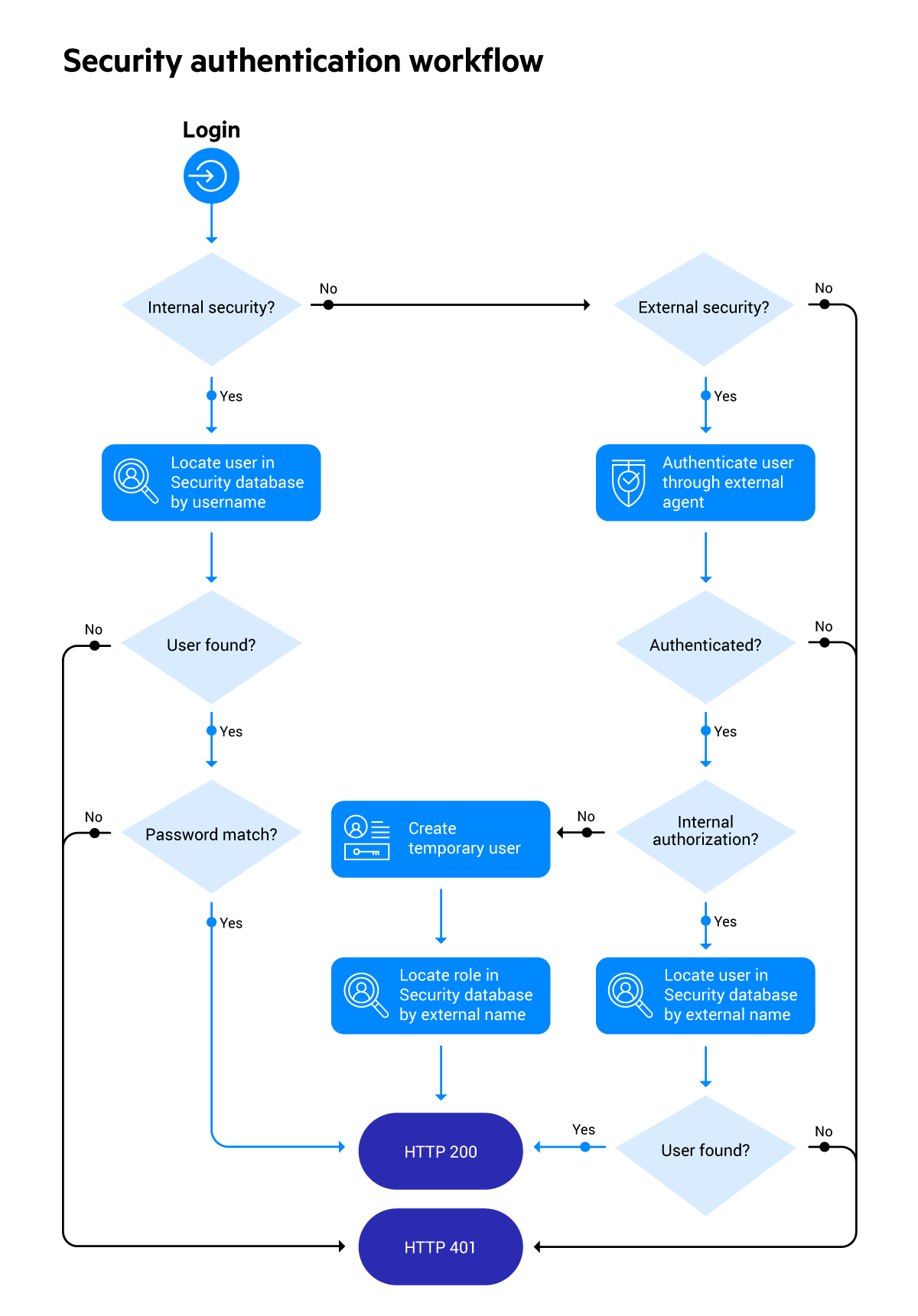
Successful Internal User Authentication Flow
When a user logs into an app server, MarkLogic Server checks if the app server is set for internal security. If so, MarkLogic Server searches the Security database for a matching username. If one is found, and the passwords match, then the internal user is authenticated. Authentication is complete.
Successful External User Authentication Flow
If the app server is configured for external security, then MarkLogic Server passes the login information to the configured external agent. The external agent sends a response containing information about the matching user. Authentication is complete, but authorization is also required.
Successful Internal Authorization Flow
If external security is configured for internal authorization, then MarkLogic Server extracts certain information from the authentication response and finds an internal user whose external name matches that information. Authorization is complete.
Successful External Authorization Flow
If the external security object is configured for external authorization, then MarkLogic Server creates a temporary user. MarkLogic Server then extracts certain information from the authentication response and finds any roles whose external names match that information. Finally, MarkLogic Server assigns each matching role to the temporary user. Authorization is complete.