Access Control Based on Client IP Address
MarkLogic Server supports deployments in which a user is automatically given access to the application based on the client IP address.
Consider a scenario in which a user is automatically logged in if he is accessing the application locally (as local-user) or from an approved subnet (as site-user). Otherwise, the user is asked to login explicitly. The steps below describe how to configure MarkLogic Server to achieve this access control.
Using the Admin Interface, configure the app server to use a custom login page:
Go to the Configuration tab for the HTTP or WebDAV app server for which you want to create a custom login page.
Scroll down to the authentication field and select
application-level.For this example, choose
nobodyas the default user. Thenobodyuser is automatically created when MarkLogic Server is installed. It is created with the following roles:rest-reader,rest-extension-user,app-user,harmonized-readerand is given a password, which is randomly generated.
Define
try-ip-login():Create a file named
login-routine.xqyand place the file in theModulesdirectory within the MarkLogic Server program directory. You create an amp fortry-ip-login()inlogin-routine.xqyin the next code sample. For security reasons, all amped functions must be located in the specifiedModulesdirectory or in theModulesdatabase for the app server.Add the following code to
login-routine.xqy:xquery version "1.0-ml" module namespace widget ="http://widget.com"; declare function widget:try-ip-login( ) as xs:boolean { let $ip := xdmp:get-request-client-address() return if(fn:compare($ip,"127.0.0.1") eq 0) then (:local host:) xdmp:login("localuser",()) else if(fn:starts-with($ip,"<approved-subnet>")) then xdmp:login("site-user",()) else fn:false() };
If the user is accessing the application from an approved IP address,
try-ip-login()logs in the user with usernamelocal-userorsite-useras appropriate and returnstrue. Otherwise,try-ip-login()returnsfalse.Note
In the code snippet above, the empty sequence () is supplied in place of the actual passwords for
local-userandsite-user. The pre-definedxdmp-loginexecute privilege grants the right to callxdmp:login()without the actual password. This makes it possible to create deployments in which users can be automatically logged in without storing user passwords outside the system.Add the following code snippet to the beginning of the default page displayed by the application, for example,
default.xqy.xquery version "1.0-ml"; import module namespace widget = "http://widget.com" at "/login-routine.xqy"; let $login := widget:try-ip-login() return if($login) then <html> <body> The protected page goes here. You are {xdmp:get-current-user()} </body> </html> else xdmp:redirect-response("login.xqy")Finally, to ensure that the code snippet above is called with the requisite
xdmp-loginprivilege, configure an amp fortry-ip-login():Using the Admin Interface, create a role called
login-role.Assign the pre-defined
xdmp-loginexecute privilege tologin-role. Thexdmp-loginprivilege gives a user of thelogin-rolethe right to callxdmp:login()for any user without supplying the password.Create an amp for
try-ip-loginas shown below:
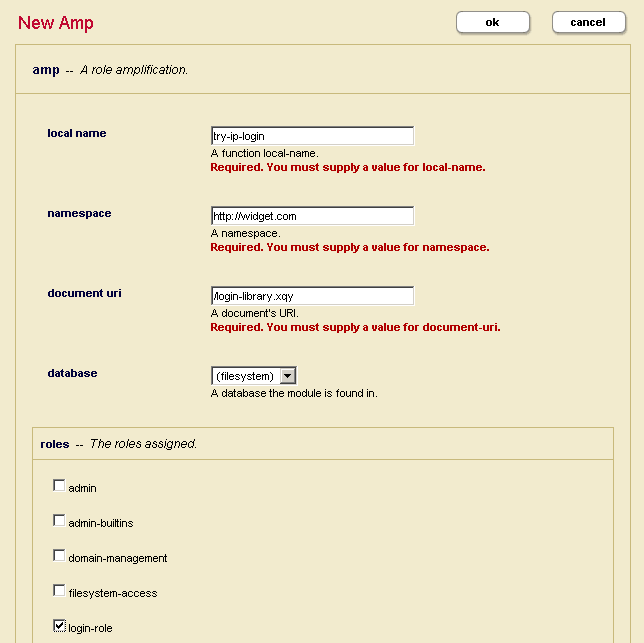
An amp temporarily assigns additional role(s) to a user only for the execution of the specified function. The amp above gives any user who is executing
try-ip-login()thelogin-roletemporarily for the execution of the function.In this example,
default.xqyis executed asnobody, the default user for the application. Whentry-ip-login()is called, thenobodyuser is temporarily amped to thelogin-role. Thenobodyuser is temporarily assigned thexdmp-loginexecute privilege by virtue of thelogin-role. This enablesnobodyto callxdmp:login()intry-ip-login()for any user without the corresponding password. Once the login process is completed, the user can access the application with the permissions and privileges oflocal-userorsite-useras appropriate.The remainder of the example assumes that
local-userandsite-usercan access all the pages and functions within the application.Create a role called
application-user-role.Create an execute privilege called
application-privilege. Add this privilege to theapplication-user-role.Add the
application-user-roletolocal-userandsite-user.Add this snippet of code before the code that displays each of the subsequent pages in the application:
try { xdmp:security-assert("application-privilege","execute") ... } catch($e) { xdmp:redirect-response("login.xqy") }or
if(not(xdmp:has-privilege("application-privilege","execute"))) then ( xdmp:redirect-response("login.xqy") ) else ()
This ensures that only the user who has the
application-privilegeby virtue of his role can access these protected pages.