Roles, Privileges, Document Permissions, and Users
Privileges, document permissions, and users all interact with roles to define your security policies. The following diagram shows an example of how these entities interact.
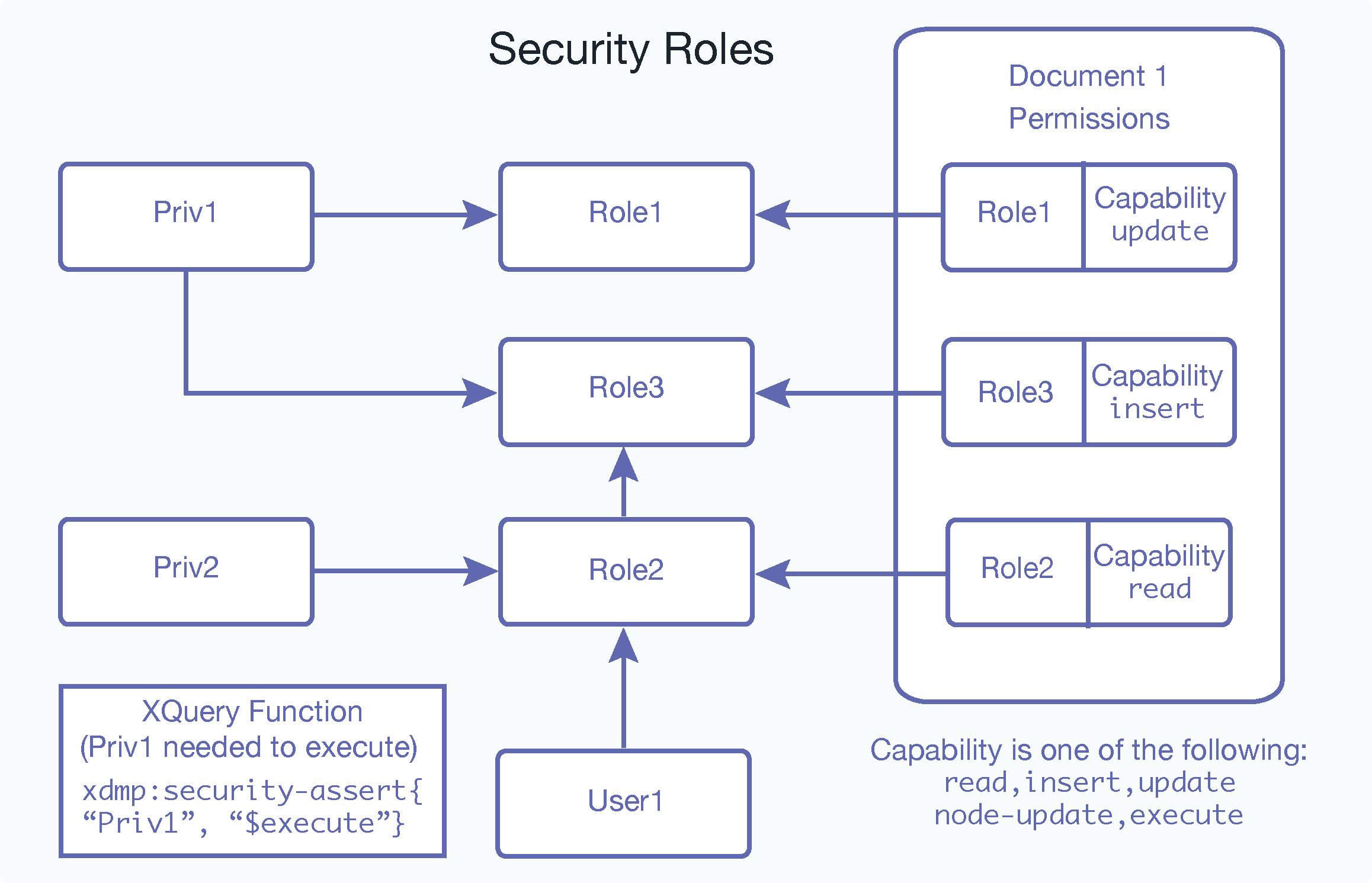
Notice how all of the arrows point into the roles; that is because the roles are the center of all security administration in MarkLogic Server. In this diagram, User1 is part of Role2, and Role2 inherits Role3. Therefore, even though User1 has only been assigned Role2, User1 possesses all of the privileges and permissions from both Role2 and Role3. Following the arrows pointing into Role2 and Role3, you can see that the user possesses Priv1 and Priv2 based on the privileges assigned to these roles and insert and read capabilities based on the permissions applied to Document1.
Because User1 possesses Priv1 (based on role inheritance), User1 is able to execute code protected with a xdmp:security-assert("Priv1", "execute") call; users who do not have the Priv1 privilege cannot execute such code.