Configuring an App Server for External Authentication
This section describes how to configure an App Server for external authentication.
Click Groups in the left tree menu.
Click the group in which you want to create or configure the App Server (for example, Default).
Click App Servers on the left tree menu.
Select the Create HTTP tab to create a new App Server, or select an existing App Server from the Summary page.
In the App Server Configuration page, scroll down to the authentication section and set the fields, as described in the table below.
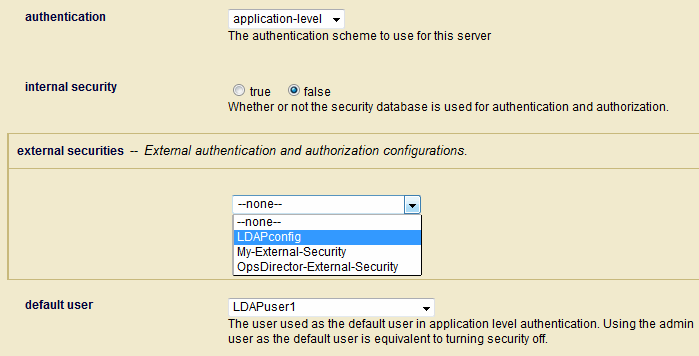
Field |
Description |
|---|---|
authentication |
The authentication scheme: |
internal security |
Determines whether or not authentication for the App Server is to be done internally by MarkLogic Server. |
external security |
The name of the external authentication configuration object to use. For details on how to create an external authentication configuration object, see Creating an External Authentication Configuration Object. To set additional external authentication configuration objects, click on NoteIf you have configured an App Server with multiple external configuration objects that use LDAP, the LDAP server specified by the first configuration object (the object at the top of the list) is always used first. If this first LDAP server is unresponsive, the second LDAP server will not be tried until the first LDAP server exceeds the time-out period established by |
default user |
If you select |