Cluster Encryption Options
You can either configure encryption for the embedded keystore (the PKCS #11 secured wallet) or for an external KMIP-compliant keystore using the Admin Interface. Use the Edit Keystore Configuration page to configure encryption at rest for a cluster. Using this page, you can configure data encryption, configuration file encryption, or encryption of log files.
To configure encryption using the embedded keystore in the Admin Interface, click Clusters in the left navigation tree and click the name of the cluster you want to configure.
Click the Keystore tab to configure the keystore for encryption at rest.
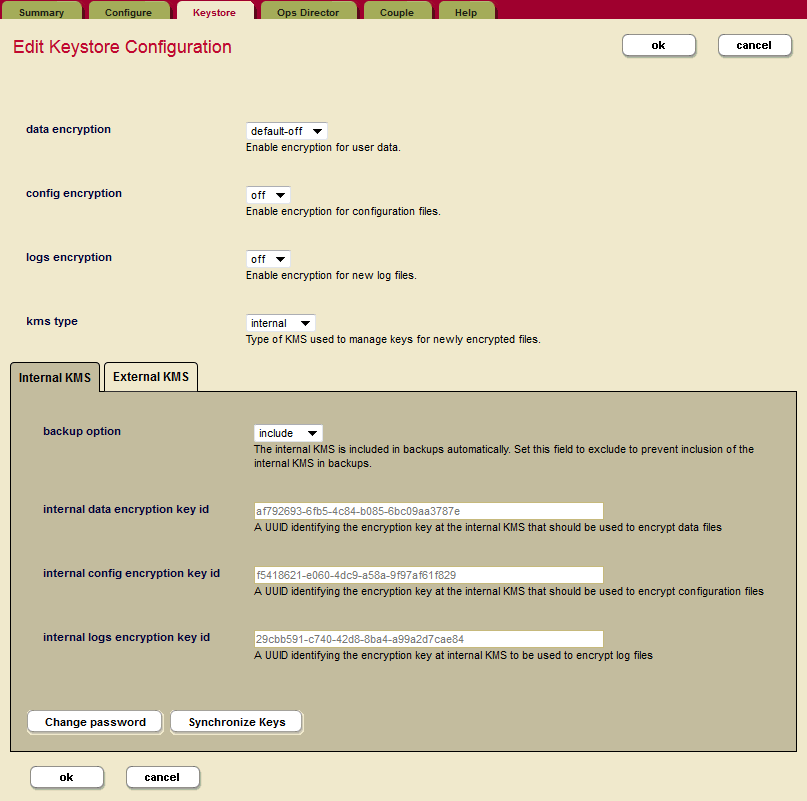
Use the drop-down menus to configure encryption for data, config files, and/or log files.
Setting
Description
data encryption
Specifies whether or not encryption is enabled for user data. These are the options:
force— Force encryption for all data in the cluster. The database configuration cannot overwrite this setting.default-on— By default encryption is on. The database configuration can overwrite this setting.default-off— By default encryption is off. The database configuration can overwrite this setting.config encryption
Specifies whether or not encryption is enabled for configuration files.
logs encryption
Specifies whether or not encryption is enabled for log files.
kms type
Specifies whether the KMS is internal to MarkLogic Server or an external KMS.
A keystore is a secure location where the actual encryption keys used to encrypt data are stored. The keystore for encryption at rest is a key management system (KMS). This keystore can be either the MarkLogic Server embedded PKCS #11 secured wallet, or an external third party KMS.
Beneath these options on the Edit Keystore Configuration page, there are two tabs for specifying further options for either the Internal KMS or the External KMS. For the Internal KMS there are these options:
Setting
Description
backup option
The internal KMS is automatically included in backups unless you change the default setting of “include” to “exclude”.
internal data encryption key id
The UUID that identifies the encryption key from the internal KMS that is to be used to encrypt data files.
internal config encryption id
The UUID that identifies the encryption key from the internal KMS that is to be used to encrypt config files.
internal logs encryption id
The UUID that identifies the encryption key from the internal KMS that is to be used to encrypt log files.
Click OK when you are done.
Note
Adding or changing any encryption information will require a restart of all of the hosts in the cluster.