High Availability and Failover with External KMS
Encryption at rest enables you to specify multiple hosts, multiple ports, and multiple KMIP credentials to connect to KMIP servers. The information to connect to these servers is specified in the fields on the external Key Management Service (KMS) section of the Edit Keystore Configuration page. The information must be validated at configuration time. For each host with specified, if there must exist a PEM-encoded Certificate Authority file and a PEM-encoded KMIP certificate file accessible to each node of the MarkLogic Server.
For each host specified, there must exist a PEM-encoded Certificate Authority file and PEM-encoded KMIP certificate file accessible to each node of MarkLogic Server.
The PEM files are looked up with the user-specified path or default location for the first host. For subsequent hosts, the file names are expected to be accessible through the original file name pre-pended by the host’s index in the configuration sequence.
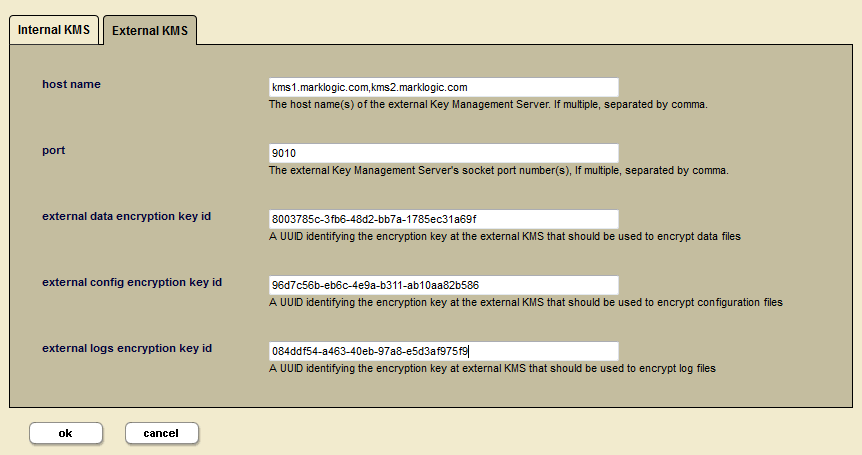
For example, if
the configured host names are
kms1.marklogic.comandkms2.marklogic.com,the configured port is
9010,the specified CA file is at
path/CA.pem, andthe specified certificate file is at
/path/cert.pem,
then, the configuration must be validated through the following:
File
/path/CA.pem,/path/1-CA.pem,/path/cert.pem, and/path/1-cert.pemall exist.The user-specified encryption keys can be validated through connecting to
kms1.marklogic.comat port9010.The user-specified encryption keys can be validated through connecting to
kms2.marklogic.comat port9010.
If the first specified KMIP host stops responding, the program will try to connect to each of the other hosts on the user-specified list in turn until it successfully connects.
If for some reason the program is unable to connect with a valid KMIP server after multiple attempts, it will report an exception.