Add Protected Paths and Query Rolesets
Using the Admin Interface, add the protected paths and query rolesets to the Security database. If no query rolesets are configured, a query will only match documents by the terms that are visible to everyone.
To start, check for any existing protected paths using this query in the Query Console:
(: run this query against the Security database :)
fn:collection("http://marklogic.com/xdmp/protected-paths")
This will return an empty sequence if there are no protected paths. If there are protected paths, information about those protected paths will be displayed, including the path ID, the path expression, the permissions, and roles associated with that path.
Using the Admin Interface, add protected paths with permissions for els-user-2. To add the protected path from the Admin Interface:
Click Security in the left tree menu.
Click Protected Paths and then click the Create tab.
Enter the path expression for the first path (
/root/bar[@baz=1]),with read permissions forels-role-2.![Screenshot illustrating the Path Expression field with /root/bar[@baz=1] filled in](../../image/1668554c3c32b1.gif)
Grant read permissions. Under role name + capacity, from the first drop-down, select
els-role-2, and from the second drop down, select read.Click OK when you are done. Since there are no namespaces in these examples, the prefix and namespace are not required for the protected path.
For examples using namespaces and prefixes as part of a protected path, see Namespaces as Part of a Protected Path.
Repeat this for two additional protected paths, “test” and “/root/reg[fn:matches(@expr, 'is')]”.
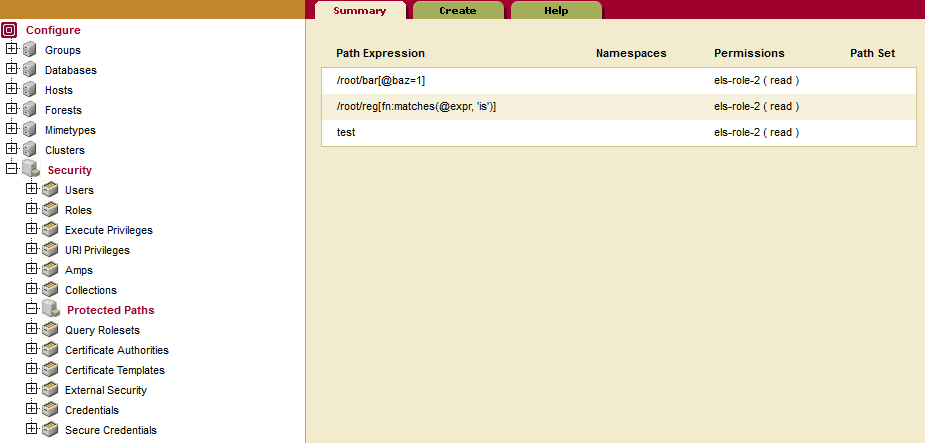
The three protected paths with read permissions for els-role-2 are these:
/root/bar[@baz=1]test/root/reg[fn:matches(@expr, 'is')]
Alternatively, you can add these protected paths with the Query Console. Use this code to add these protected paths with permissions for els-user-2 to the Security database:
(: add protected paths -> run against the Security database :)
xquery version "1.0-ml";
import module namespace sec="http://marklogic.com/xdmp/security"
at "/MarkLogic/security.xqy";
sec:protect-path("/root/bar[@baz=1]", (), (xdmp:permission("els-role-2", "read"))),
sec:protect-path("test", (), (xdmp:permission("els-role-2", "read"))),
sec:protect-path("/root/reg[fn:matches(@expr, 'is')]", (), (xdmp:permission("els-role-2", "read")))
=> Returns three numbers representing the protected paths
Note
Adding, unprotecting, or changing permissions on protected paths will trigger reindexing. This reindexing will only apply to documents that include or match the paths.
Now add query rolesets for these documents. In the Query Console, run this code to add query rolesets for els-user-2:
(: run this against the Security database :)
xquery version "1.0-ml";
import module namespace sec = "http://marklogic.com/xdmp/security"
at "/MarkLogic/security.xqy";
let $qry := 'xdmp:database-node-query-rolesets(fn:doc(), ("all"))'
let $qry-rolesets :=
xdmp:eval($qry, (),<options xmlns="xdmp:eval">
<database>{xdmp:database('Documents')}</database>
</options>)
return
sec:add-query-rolesets($qry-rolesets)
In most cases you will want to use the helper functions (xdmp:database-node-query-rolesets and xdmp:node-query-rolesets) to create query rolesets. The helper function automatically created the query rolesets based on the protected paths you have set. See Helper Functions for Query Rolesets for more information. To understand more about query rolesets, see Query Rolesets.
You can also add query rolesets manually with XQuery in the Query Console if you only have a few query rolesets to add. Run this code against the Security database:
(: add query rolesets => run against the Security database :)
xquery version "1.0-ml";
import module namespace sec="http://marklogic.com/xdmp/security"
at "/MarkLogic/security.xqy";
let $roleset := sec:query-roleset("els-role-2")
return
sec:add-query-rolesets(sec:query-rolesets($roleset))
=>
Returns a unique ID representing the added query rolesets
Note
Adding query rolesets does not trigger reindexing, since it is only used by queries.
Check for query rolesets in the Security database using the Query Console:
(: run this query against the Security database :)
fn:collection("http://marklogic.com/xdmp/query-rolesets")
=>
Returns details about query rolesets in the Security database.
There is also a collection for protected paths in the Security database:
(: run this query against the Security database :)
fn:collection("http://marklogic.com/xdmp/protected-paths")
=>
Returns details about protected paths in the Security database.
The els-role-2 can now see the elements in these paths, but the els-user-1 cannot:
test/root/bar[@baz=1]/root/reg[fn:matches(@expr, 'is')]