Security Entities
The key entities in MarkLogic Server’s security model are:
User
A user within the model has a set of roles. A user has privileges and permissions within the system based on the roles he is given.
Role
A role gives privileges and permissions to a user. A role may inherit from multiple roles. Role inheritance is an “is-a” relationship. Hence, an inherited role also has the privileges and permissions of its parent(s).
Execute Privilege
An execute privilege grants authorization to perform a protected action. Only roles (and their inherited roles) specified in the execute privilege can perform the action.
URI Privilege
A URI privilege grants authorization to create a document within a protected base URI. Only roles (and their inherited roles) specified in the URI privilege can create the document within the protected base URI.
Permission
A permission protects a document or a collection. Each permission associates a single role with a capability (Read, Update, Insert). A protected document or collection has a set of associated permissions.
Collection
A collection groups a set of documents that are related. A document may belong to any number of collections. A collection exists in the system when a document in the system states that it is part of that collection. However, an associated collection object is not created and stored in the Security database unless it is protected.
Permissions created at the collection level apply to the collection but not to documents within the collection. A user needs to have permissions at the both the collection and document level to be able to add documents to a protected collection.
Amp
An amp gives the User additional roles temporarily while the user is performing a certain task (executing a function).
Certificate Authority
A certificate authority (CA) is a trusted third party that certifies the identity of entities, such as users, databases, administrators, clients, and servers. A CA is used by the SSL (Secure Sockets Layer) security standard to provide encrypted protection between browsers and App Servers. When an entity requests certification, the CA verifies its identity and grants a certificate, which is signed with the CA's private key. If the CA is trusted, then any certificate it issues is trusted unless it has been revoked. For details on SSL support in the MarkLogic Server, see Configuring SSL on App Servers in Securing MarkLogic Server.
Certificate Template
A certificate template is a MarkLogic construct that is used to generate certificate requests for the various hosts in a cluster. A certificate template is used by the SSL (Secure Sockets Layer) security standard to provide encrypted protection between browsers and App Servers. The template defines the name of the certificate, a description, and identity information about the owner of the certificate. For details on SSL support in the MarkLogic Server, see Configuring SSL on App Servers in Securing MarkLogic Server.
External Authentication
An External Authentication Configuration Object is used to configure MarkLogic Server for external authentication by LDAP, Kerberos, or SAML. An external authentication configuration object specifies which authentication protocol and authorization scheme to use, along with any other parameters necessary. For details on external authentication with MarkLogic Server, see External Security in Securing MarkLogic Server.
Security Entity Relationships
The following diagram illustrates the relationships between the different entities in the MarkLogic Server security model.
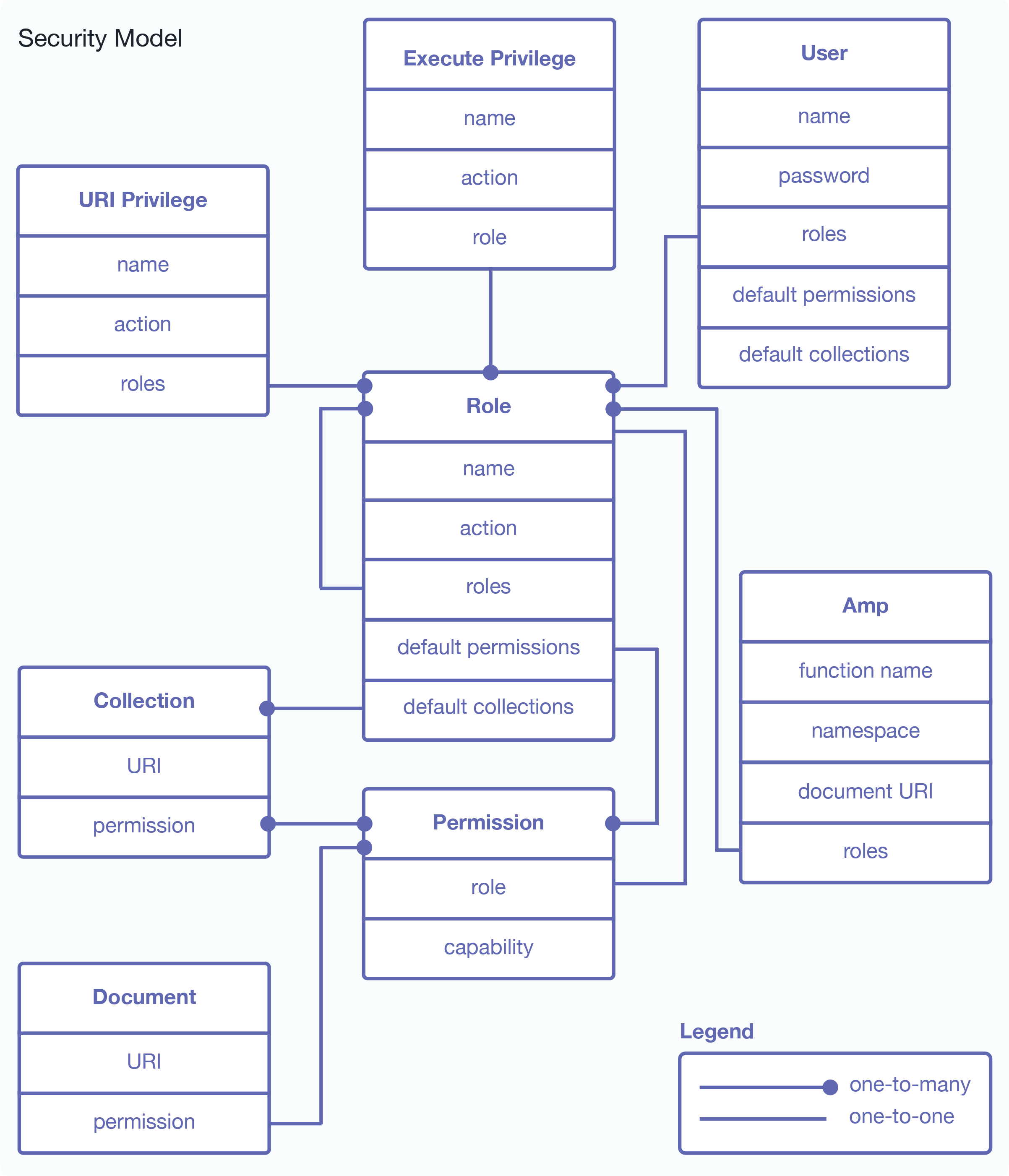
The remaining sections detail the procedures to administer MarkLogic Server security entities. All security administrative tasks are “hot”— the changes take effect immediately without a server restart.
Permissions are not administered through the administrative interface and are not described in detail in this document. For more information on using permissions in MarkLogic Server, see the XQuery and XSLT Reference Guide.