ALB Ingress
This approach uses the ALB Ingress Controller functionality provided by EKS.
Note
This approach will not address ODBC exposition, as ALB Ingress only supports HTTP/HTTPS connections. See ODBC connection through Ingress in EKS for further information.
ALB Ingress limitations
100 total rules per application load balancer.
Typically, only 100 Ingresses per ALB.
5 condition values per rule.
5 wildcards per rule.
5 weighted target groups per rule.
Only HTTP/HTTPS protocol.
Install ALB Ingress
To install ALB Ingress, see AWS Load Balancer Controller installation.
Note
To use External DNS, see Setup External DNS.
This feature is still in alpha release and should not be used in production.
Ingress definition
When you install ALB Ingress, the Ingress definition automatically creates an ALB.
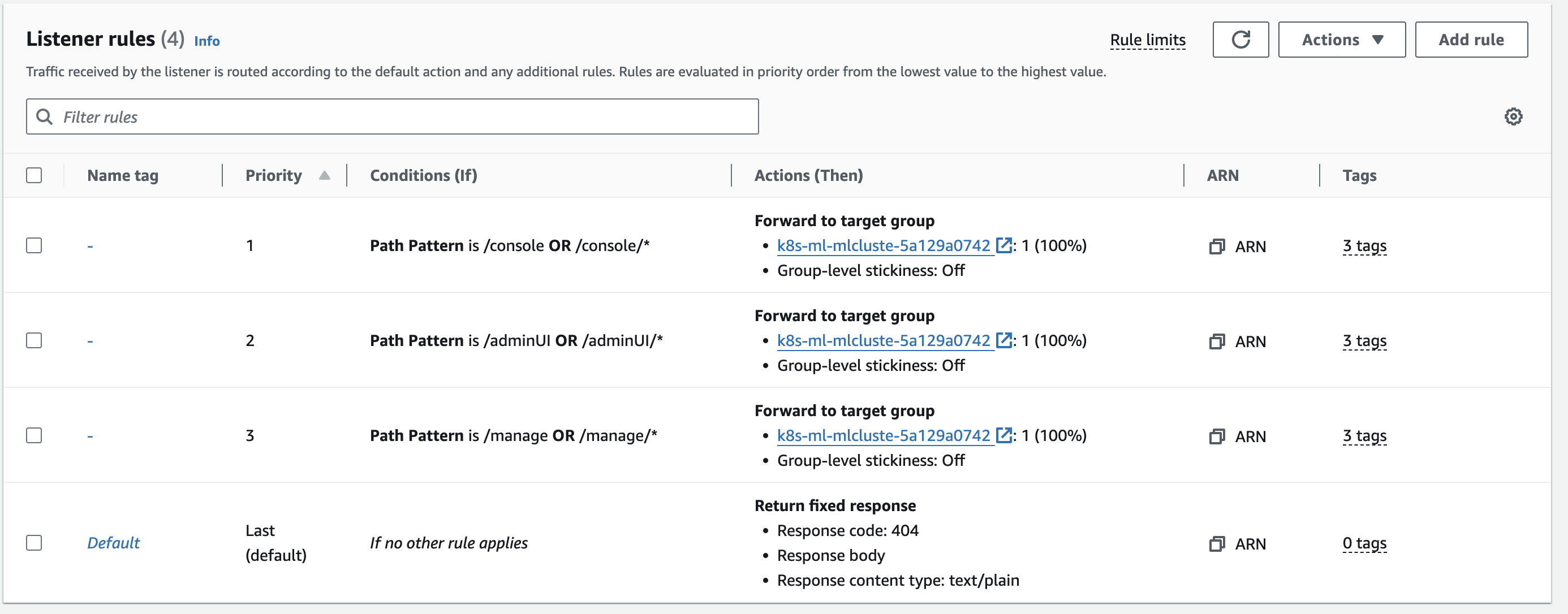
Configure the paths
To configure the paths, use these values in the values.yaml file in the HAProxy section of the Helm Chart:
# Used if MarkLogic Default APP-Servers are meant to be exposed under subpath different from /
#######################################################################
# IMPORTANT NOTE: #
# This feature is only supported with MarkLogic 11.1 and higher. #
# See Limitations and known Issues in the README file. #
#######################################################################
pathbased:
enabled: true
# This the default listening port in the Front-End section of the HAProxy when using Path based routing
frontendPort: 443
# Path and port used on HAProxy
# The same path will be used on Ingress for Default AppServers
defaultAppServers:
appservices:
path: /console
port: 8000
admin:
path: /adminUI
port: 8001
manage:
path: /manage
port: 8002
Configure the Ingress definition
The Ingress definition can be configured in the values.yaml file:
## Configure Ingress
#######################################################################
# IMPORTANT NOTE: #
# Ingress is only supported with MarkLogic 11.1 and higher. #
# See Limitations and known Issues in the README file. #
#######################################################################
## ref: https://kubernetes.io/docs/concepts/services-networking/ingress/
ingress:
enabled: true
## Ingress class
## ref: https://kubernetes.io/docs/concepts/services-networking/ingress/#ingress-class
className: "alb"
## Ingress labels
## ref: https://kubernetes.io/docs/concepts/overview/working-with-objects/labels/
labels:
app.kubernetes.io/instance: marklogic
app.kubernetes.io/name: ml
## Ingress annotations
## ref: https://kubernetes.io/docs/concepts/overview/working-with-objects/annotations/
annotations:
alb.ingress.kubernetes.io/healthcheck-port: '443'
alb.ingress.kubernetes.io/healthcheck-path: /adminUI
alb.ingress.kubernetes.io/success-codes: '200-401'
alb.ingress.kubernetes.io/load-balancer-name: ml
alb.ingress.kubernetes.io/scheme: internet-facing
alb.ingress.kubernetes.io/listen-ports: '[{"HTTPS":443}]'
alb.ingress.kubernetes.io/target-group-attributes: load_balancing.algorithm.type=least_outstanding_requests
alb.ingress.kubernetes.io/certificate-arn: arn:aws:acm:us-west-2:XXXXXXXXXXX:certificate/XxXXXXXX-xxxx-XXXX-XXXX-XXXXXXXxxxxXXX
alb.ingress.kubernetes.io/target-type: ip
alb.ingress.kubernetes.io/group.name: ml-group
alb.ingress.kubernetes.io/load-balancer-attributes: idle_timeout.timeout_seconds=600,routing.http.xff_header_processing.mode=append
Note
The path definition of the Ingress will be the same as defined in the HAProxy section.
Configuration details
Code |
Description |
|---|---|
alb.ingress.kubernetes.io/healthcheck-port |
Specifies the port on which to perform the health check. |
alb.ingress.kubernetes.io/healthcheck-path |
Specifies the path used for the health check. |
alb.ingress.kubernetes.io/load-balancer-name: ml |
Specifies the prefix for the name of the ALB. Note that name impacts the entire IngressGroup. |
alb.ingress.kubernetes.io/scheme: internet-facing |
Specifies the scheme. Because MarkLogic app-servers should be exposed from outside of the cluster and outside of the cloud, this is set it to internet-facing. |
alb.ingress.kubernetes.io/listen-ports |
Specifies the listening port for each Ingress. The syntax is : <protocol>:<port>. Protocol can only be HTTP or HTTPS. |
alb.ingress.kubernetes.io/target-group-attributes |
Specifies the target group attributes as the load balancing algorithm. |
alb.ingress.kubernetes.io/certificate-arn |
Specifies the certificates to be used (HTTPS termination on the ALB should be enabled). |
alb.ingress.kubernetes.io/target-type |
Specifies the target type. The target type can be instance or ip. instance type is only available if the target service is type NodePort. |
alb.ingress.kubernetes.io/group.name |
Specifies the group name for the ALB. This allows several Ingresses to use the same ALB. group.name and load.balancer.name have to be the same in the same IngressGroup. |
For additional annotations, see the complete list.
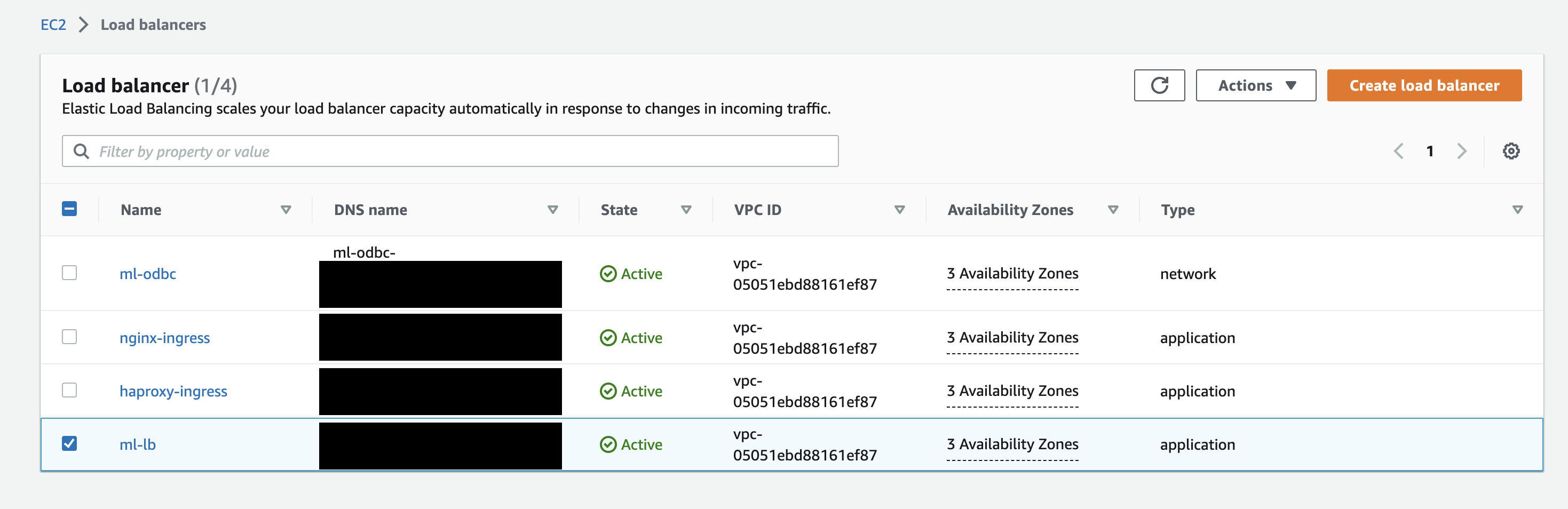
Check the ALB
Go to the AWS Console and check what the created ALB looks like:
Route53
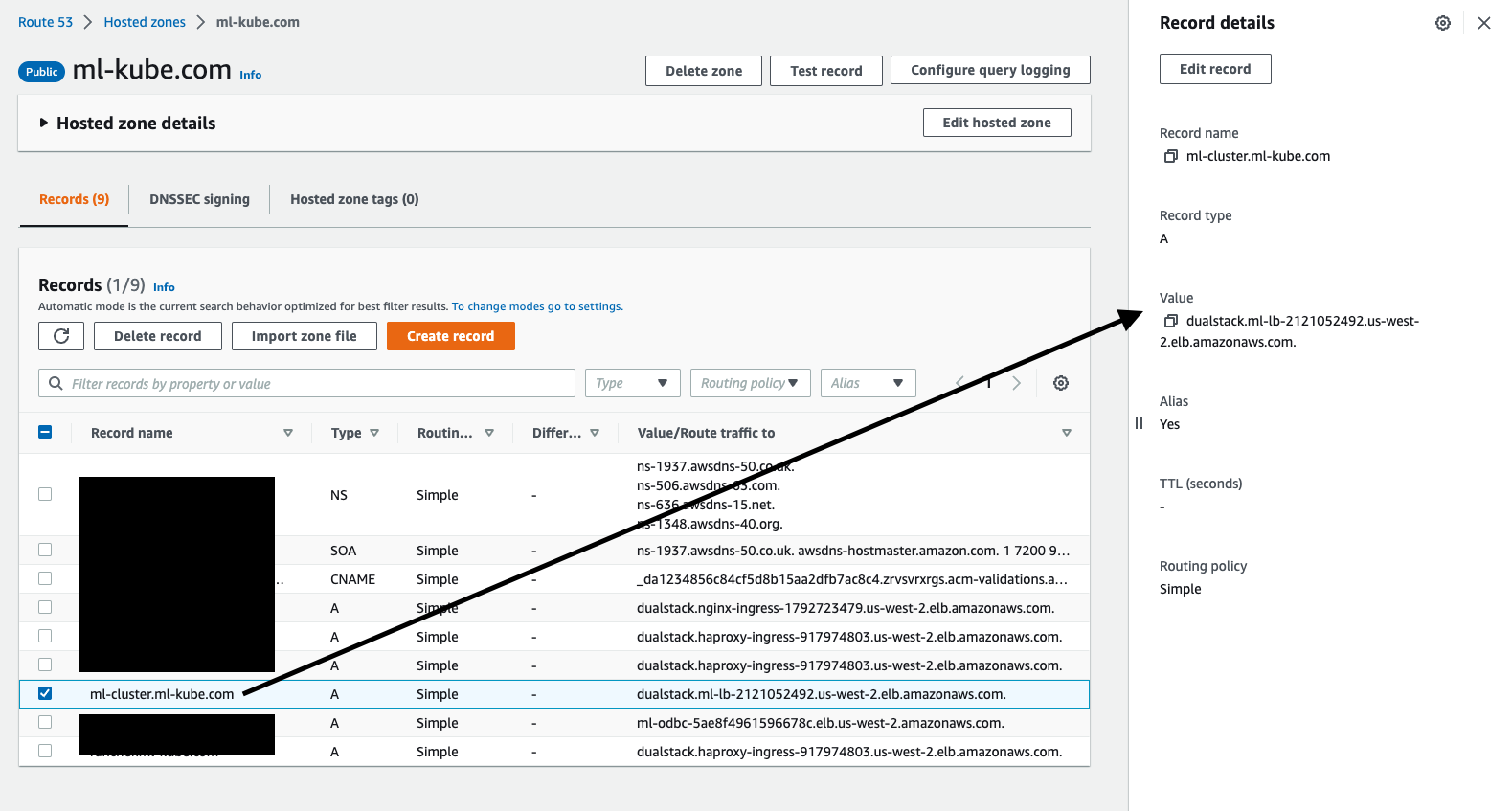
Because the ALB scheme is specified as internet-facing, the automatically generated DNS name can be used. However, it is more convenient to use a proper DNS name. This is done using Route53:
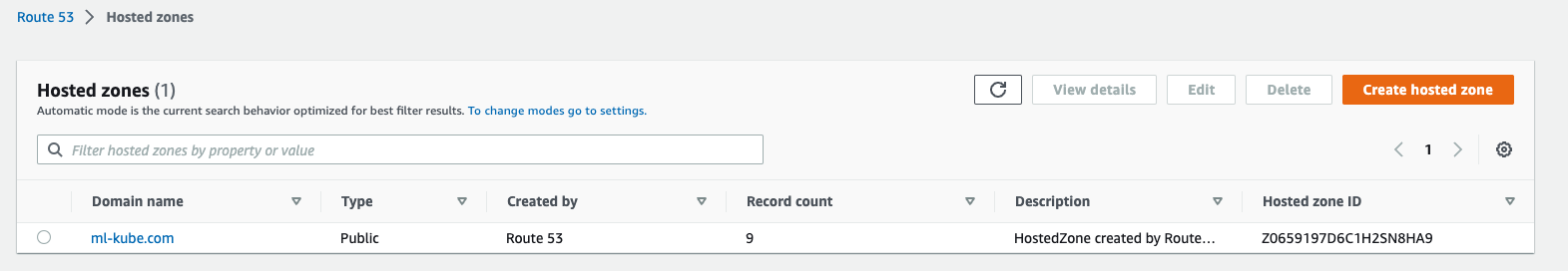
Configure Route53 with one hosted zone:
Create a dedicated record to point to the ALB: